After using the NTP (Network Time Protocol) to conduct amplified distributed denial-of-service attacks, the current trend shows that SSDP (Simple Service Directory Protocol) has gained in popularity.
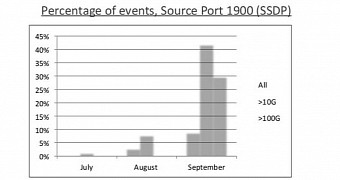
Telemetry data from Arbor Networks, a company offering distributed denial-of-service (DDoS) attack mitigation services, SSDP is accountable for 42% of the incidents above 10Gbps recorded by their systems in September.
NTP less popular, SSDP to take its place
For the entire third quarter of 2013, the company monitored almost 30,000 SSDP-based DDoS attacks, the largest of them peaking at 124Gbps.
SSDP is the protocol used for the discovery of Plug & Play devices through port 1900, and it is currently used by routers and network devices. The attack’s bandwidth amplification factor by leveraging SSDP is of 30.8 times, much lower than NTP, which can amplify more than 500 times.
“Everyone is aware of the huge storm of NTP reflection DDoS attacks in Q1 and early Q2, but although NTP reflection is still significant there isn’t as much going on now as there was – unfortunately, it is looking more and more like SSDP will be the next protocol to be exploited in this way,” Darren Anstee, Director of Solutions Architects at Arbor Networks said in a statement on Tuesday.
As far as SSDP is concerned, the most targeted countries were the US (19.1%), France (10%) and Denmark (7.4%).
Important to note is the fact that this protocol has been used only three times for DDoS attacks in the second quarter of the year, but in Q4 the interest of cybercriminals grew exponentially, being involved in no less than 29,506 attacks, accounting for 4% of all incidents for the same period of time.
Largest DDoS attack in 2014 had its target in France
The company monitored other DDoS attack types and concluded that those relying on NTP reflection have decreased, although half of those over 100Gbps were still NTP-based.
The largest incident recorded by Arbor Networks for Q3 2014 reached 264.4Gbps in size. So far in 2014, the largest attack is one directed towards a victim in France and lasted for four hours and 22 minutes, being 325Gbps in size; it was NTP-based.
“Organizations should take heed and ensure that their DDoS defense is multi-layered, and designed to deal with both attacks that can saturate their connectivity, and more stealthy, sophisticated application layer attacks,” Anstee said.
A reflected attack involves the attacker sending a request to a server spoofing the IP address of the target. After processing the request, the server returns the response to the spoofed IP; if the request is returned to a single recipient from multiple machines, a denial-of-service condition is created.
Amplification is achieved if the server replying to the request from the spoofed IP returns more data than the original input, thus increasing the traffic volume from a single source. By leveraging multiple sources, a distributed denial-of-service attack is created.
 14 DAY TRIAL //
14 DAY TRIAL //