Without a doubt, ZeuS is the most notorious banking Trojan in the world. However, until recently, the threat didn’t have a 64-bit version.
Security researchers from Kaspersky say that the 64-bit ZeuS might have been compiled as early as April 2013, with the first samples being spotted in the wild around June.
The 64-bit version of ZeuS works just like the 32-bit version. Its main goal is to steal personal and financial information from infected computers.
However, the new variant is also capable of communicating with its command and control servers via the TOR network. This functionality was implemented in other pieces of malware some time ago, but ZeuS has lacked such capabilities until now.
The new piece of malware is actually maintained inside a 32-bit version. The threat injects malicious code into certain processes. If the targeted process is the one of a 64-bit application, the 64-bit ZeuS steps into play.
The existence of the 64-bit ZeuS is an important thing, especially since this represents a new milestone in the Trojan’s evolution. However, considering that most users still run the 32-bit versions of web browsers, it doesn’t do much difference.
So why develop the new variant, especially since it’s not exactly an easy task? Experts believe that this might simply be a marketing ploy. A lot of potential buyers might be attracted by the idea of a 64-bit version that communicates over Tor.
Another reason for developing the 64-bit version is that it might represent the groundwork for future needs. For instance, the current version still has some bugs, experts say.
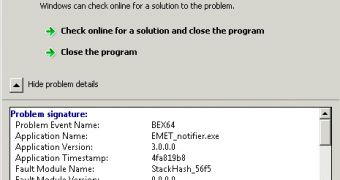
“When ZeuS injects a 64-bit counterpart into the 64-bit process of the EMET Notifier application it causes this process to crash,” Kaspersky Lab Expert Dmitry Tarakanov noted in a blog post.
For additional technical details on the 64-bit ZeuS, check out Kaspersky’s blog.
 14 DAY TRIAL //
14 DAY TRIAL //