A fresh version of the PushDo malware component has been detected by security researchers to have changed the encryption keys for the communication across the botnet or with the command and control server.
Malware writers have created several variants of the PushDo Trojan, and researchers at Bitdefender have found a new one that relies on the same communication protocol, but switched to different private and public encryption keys.
Another modification is the fact that the fresh revision of the malware contains an encrypted overlay for the binaries, which would have a validation purpose. “If the conditions specified in the overlay aren’t met, the sample doesn’t run properly,” explain the researchers in a post on Bitdefender’s blog.
It seems that the list of the domain names issued through the built-in domain generation algorithm (DGA) now contains about 100 clean entries. The DGA component is designed to hide the details for the real control and command server, making the botnet more difficult to disrupt.
Bitdefender informs that a new DGA is in place, maintaining the old structure of the algorithm but with a different pattern for the domain names generated. The security company managed to sinkhole one of them, and the result was that 2,336 unique IP addresses connected to the server in less than three hours.
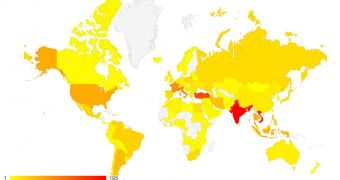
According to Bitdefender, India, Vietnam, and Turkey are the countries with the largest number of PushDo infections.
The investigation is under way at the moment and no additional details have been provided by the security researchers.
 14 DAY TRIAL //
14 DAY TRIAL //