Security experts from FireEye have been monitoring the activities of a cybercrime group that uses various types of malware in its operations.
There are two major types of cybercriminals: ones that use off-the-shelf malware to infect as many computers as possible, and sophisticated actors known for launching what’s known as Advanced Persistent Threat (APT) attacks.
However, there are more and more groups that fall in between these two categories. FireEye has analyzed the activities of one crew that appears to be targeting a wide range of organizations, including banks, financial services companies, and businesses.
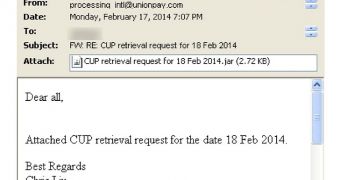
The attack starts with a typical spam email that carries an attachment. The attached file is a Java archive (.jar), but it’s not an exploit. Instead, it’s simply designed to download and run an executable.
The payload is a multi-platform remote access tool (RAT) called Netwire. Netwire has been around since 2012 and it’s being sold on underground forums for prices ranging between $40 (€29) and $140 (€101).
The server from which the RAT is downloaded is a legitimate website that has been compromised by the attackers. Experts have managed to find some other tools and malware on it.
For instance, they’ve found a tool that’s used to extract email addresses. Over 8,500 email addresses have been identified. They are hosted on 1,351 domains belonging to various types of companies in Asia and the Middle East.
On the server, researchers have discovered a statistics package which shows that the malicious executable has been downloaded 802 times, which means that over 9% of the targets opened the attachment in the spam email.
Netwire is not the only threat used by this cybercrime group. Experts have also spotted DarkComet RAT, the free RAT whose developer has decided to stop working on it after seeing that his creation is abused for malicious purposes.
In addition to RATs, FireEye has uncovered point-of-sale (POS) malware, namely JackPOS. The threat is designed to steal payment card data from infected systems.
“We don’t know how the attackers were deploying JackPOS in this particular case, but we suspect that once targets of interest were identified using either Netwire or DarkComet, the attackers would then deploy JackPOS to steal credit card information,” FireEye experts noted in a blog post.
The notorious banking Tojan ZeuS has also been utilized by the attackers. Another Trojan, which the cybercriminals use to take full control of computers, is “Handsnake,” a piece of malware based on Carberp.
For additional technical details, check out FireEye’s blog.
 14 DAY TRIAL //
14 DAY TRIAL //