Security researchers from Rapid 7 have identified three types of vulnerabilities which affect the Universal Plug and Play (UPnP) protocol used by devices such as PCs, printers and other Internet-enabled devices.
Experts have found that of the 80 million IPs that responded to UPnP discovery requests, between 40 and 50 million are vulnerable to at least one type of attack.
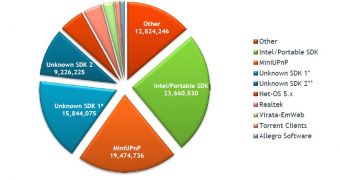
According to the whitepaper released by Rapid 7, three classes of problems have been identified: programming flaws in common UPnP discovery protocol (SSDP) implementations, exposure of the UPnP control interface (SOAP), and programming flaws in the UPnP HTTP and SOAP implementations.
“The two most commonly used UPnP software libraries both contained remotely exploitable vulnerabilities. In the case of the Portable UPnP SDK, over 23 million IPs are vulnerable to remote code execution through a single UDP packet,” Rapid 7’s HD Moore explained.
“All told, we were able to identify over 6,900 product versions that were vulnerable through UPnP. This list encompasses over 1,500 vendors and only took into account devices that exposed the UPnP SOAP service to the internet, a serious vulnerability in of itself,” he added.
Even the US Computer Emergency Readiness Team (CERT) has published an alert regarding the security holes identified in libupnp, the portable SDK for UPnP. The organization advises users to apply the latest update which addresses the vulnerabilities, restrict untrusted sources from accessing port 1900/udp, or disable UPnP altogether.
CERT has attempted to notify over 200 vendors that use the vulnerable versions of the libupnp library, including Cisco, Fujitsu, Huawei, Linksys, NEC, Siemens, Sony, Belkin, D-Link and EMC.
Rapid 7 has released a free scanner which allows users to check if their network-enabled devices are vulnerable to cyberattacks.
ScanNow for Universal Plug and Play is available for download here
 14 DAY TRIAL //
14 DAY TRIAL //