Security researchers found a vulnerable Android app that allowed an attacker to send messages to the phone and trigger various commands, without any sort of authentication.
The mobile threats team at Trend Micro discovered that the mobile app of Meituan, a Chinese site that promotes discount deals in a similar way as Groupon, would listen on TCP port 9517 in order to receive messages from a server, but the sender would not be authenticated.
Basically, a command on the phone can be triggered from any online machine once communication is established.
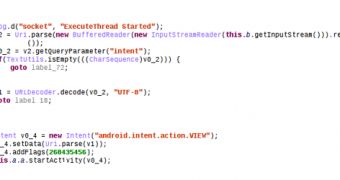
“It parses the received TCP data in a certain format and then sends android.intent.action.VIEW with the ‘intent’ in the received data,” says Veo Zhang, mobile threat analyst at Trend Micro, in a blog post about the flawed code.
As far as the risks faced by the users of a vulnerable version of the app are concerned, the analyst said that the phone could be used for sending messages to premium rate services that bring revenue to cybercriminals.
The security glitch in Meituan’s app has been removed, after the security company disclosed it privately to the affected party on June 3, allowing them time to come up with a fix and deploy a secure version of the product, two days later.
The Trend Micro security researcher also draws attention to the large number of Android apps listening on an open TCP port.
The risk presented by this is that the device is exposed online, and in lack of a firewall to monitor network communication and prevent malicious activity, it falls on the shoulder of the app developer to implement the necessary security measures that could fight against compromising the device.
However, the Android security model does not support firewall protection of any sort at the moment.
Another risk on Android is represented by vulnerabilities in Linux, the kernel the mobile platform relies on.
“Because Android is based on the Linux kernel and still uses many native Linux APIs, Linux vulnerabilities may affect Android as well. For example, CVE-2014-3153 was used by root exploit tools like TowelRoot. Another example was CVE-2014-0196,” Zhang says.
TowelRoot is a rooting app developed by Geohot, and it relies on exploiting a vulnerability in Linux futex system. Although a patch has been released for Linux, many Android versions, build 4.4 included, are still susceptible to the security flaw, which could offer administrator privileges to a potential attacker.
 14 DAY TRIAL //
14 DAY TRIAL //