The protocol used in the On-Screen Phone app on smartphones from electronics maker LG has been found to be vulnerable to authentication bypass, allowing an individual full control of the mobile device.
The On-Screen Phone app offers remote control from the computer over mobile devices from LG. Among the features of the app there is the possibility of using the phone straight from the PC for message exchange, as well as for transferring data between the two terminals.
Attacker can access any location on the phone
The phone display is mimicked on the computer, so any notification becomes available on both devices, which can be connected either via USB or through a wireless network.
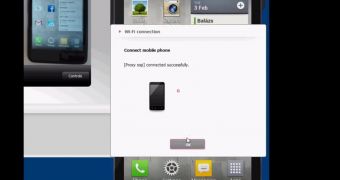
When receiving the connection request from a computer, an LG phone equipped with the app asks the owner for consent. Imre Rad, security researcher at Hungary-based SEARCH-LAB, found that the confirmation request from the phone owner can be avoided by an attacker that is on the same network as the victim.
The moment the link between the two devices is established, the controller from the PC has access to all locations on the phone, being able to plant malware for persistent surveillance or for extracting confidential financial information.
The vulnerability has been assigned the CVE-2014-8757 identifier and it affects all versions of the application starting 4.3.009.
OSP process starts automatically, cannot be stopped
Rad has created a proof-of-concept to demonstrate his findings and says that most LG smart models are affected and in many cases On-Screen Phone (OSP) comes pre-installed, without the possibility of removing it from the device since it is included as a system app.
Moreover, the researcher shows that its activity starts automatically at boot process and there is no knob to turn it off.
However, it appears the app does not create a security issue on newer smartphones released by the manufacturer. LG G3, for instance, released in June 2014, does not have OSP on it.
According to Rad, the issue lies with the fact that the server process that manages connection requests is not configured to handle them in the order they come. As such, it can be tricked to serve a different request, like starting a video stream or handling touch-screen events, before the one asking for the connection permission is delivered.
LG has already taken action to correct the issue and released version 4.3.010. Phone owners should check for the new build in LG’s Update Center and install it.
The researcher also demonstrated the validity of the flaw in a video:
 14 DAY TRIAL //
14 DAY TRIAL //