OS X users can now see if persistent items executing automatically on their machines are up to no good by receiving scan results from VirusTotal straight into KnockKnock’s interface.
KnockKnock is an open source solution built by Patrick Wardle from security startup Synack that scans OS X systems for scripts, commands, binaries or commands set to initialize with the operating system. It is the equivalent of Autoruns for Windows, created by Mark Russinovich.
Scan results are shown in the main window
In a blog post on Tuesday, VirusTotal announced that its database could also be queried by Wardle's utility.
As malware is always looking for methods to achieve persistence on a compromised machine, the tool comes in handy when trying to find illegal components.
“Malware installs itself persistently, to ensure it is automatically executed each time a computer is restarted. KnockKnock (UI) uncovers persistently installed software in order to generically reveal such malware,” reads Wardle’s description of the tool.
The current version of the utility (1.2.1) makes detecting known malware on OS X easier by integrating results from VirusTotal, Google’s online scanning service.
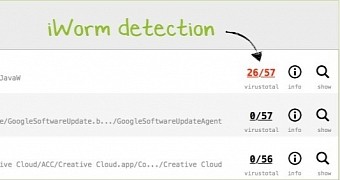
In the case of executable binaries, KnockKnock creates a hash value and sends it to VirusTotal for detection ratios. The information is then pulled in and displayed in the main window of the application next to the queried entry.
Known malware is marked in red. If there is no data available, the user can submit it to VirusTotal for analysis. A link to the full scan report is provided in KnockKnock for accessing the complete detection log.
Malicious items are identified easier and faster
A button for extensive details shows the hash, size, signed status and plist (if it’s the case) of the queried entry.
By getting information from VirusTotal, finding out if malware is available on the Apple device is no longer restricted to more advanced users.
Back in February, VirusTotal added a “Trusted Source” flag as part of a project aiming at lowering the false positive results. The mark is present in the case of items from reputable software developers, whose products have been previously checked and deemed trustworthy beyond doubt.
Patrick Wardle is the director of research and development at Synack and earlier this month he discovered a new, “yet trivial way,” to exploit the Rootpipe vulnerability, which was believed to have been addressed by Apple in the update for OS X 10.10.3.
 14 DAY TRIAL //
14 DAY TRIAL //