The amount of NTP (Network Time Protocol) servers that could be exploited for massive distributed denial-of-service attacks has decreased to over 17,000 in May, from a total of 432,120 available worldwide in December 2013.
Vulnerable NTP servers, normally used for time synchronization, can be employed to amplify a distributed denial-of-service attack (DDoS) because of the “monlist” function, which can be used to query the IP addresses of the last 600 clients that have synchronized time with the affected server.
An attacker can spoof the source IP to be the victim’s address. By abusing the “monlist” feature, the attacker can amplify the number of packets sent to a designated target even by 700 times.
The drop in the number of exploitable NTP servers comes as a result of system and network administrators updating the machines with the latest patch that disables the “monlist” command.
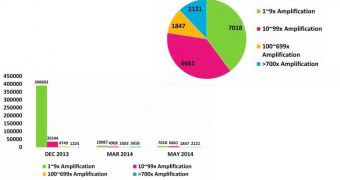
NSFOCUS, a global provider of DDoS mitigation solutions and services, ran Internet-wide scans on a constant basis and discovered that in March 2014, the vulnerable NTP servers dropped in number to 21,156.
Later on, in May, the amount of affected systems decreased to 17,647. Out of these, more than 2,100 have the necessary power for an amplification higher than 700x.
“The decline in vulnerable servers indicates that many network and system administrators have taken the necessary steps to disable or restrict monlist functions; however proper steps should be taken to ensure the rest of the vulnerable servers are protected,” says the company.
Recent events have shown the power of DDoS attacks as the activity of various services was seriously disturbed and millions of users were affected.
Feedly went through three waves of DDoS attacks; services from Ancestry.com have been disrupted, and paying customers could not meet the deadline for their projects.
A more regrettable incident started with a wave of packets and a ransom demand to stop the server flood, and ended with shutting down the business of CodeSpaces.
According to the NSFOCUS scan results, at the moment there are 7,018 NTP servers with a power of amplification of up to 10 times, 6,661 can increase the attack potential to 100 times, 1,847 have the power of up to 700 times and the rest of 2,121 can intensify a DDoS attack more than 700 times.
The report says that “if hackers were successful in accessing and amplifying the magnification capability of these NTP servers, they would still be able to stream out over 170Gbps of attack traffic. This type of high-volume attack is beyond the defense capability of most common websites and organizations.”
 14 DAY TRIAL //
14 DAY TRIAL //