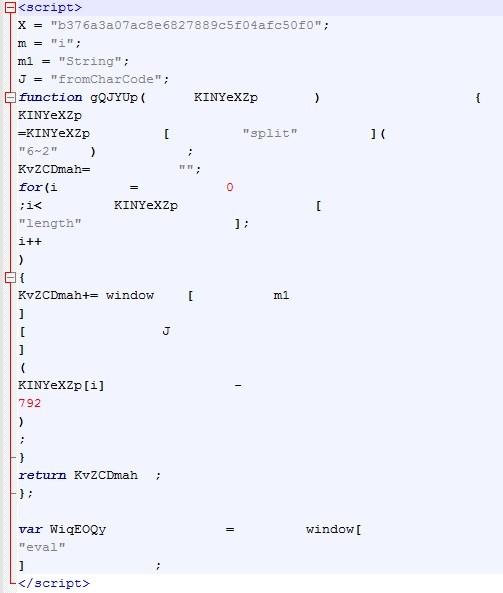
Exploit code for a vulnerability fixed by Adobe in the current version of Flash Player has been included in Nuclear exploit kit, researchers have found.
The flaw is a type confusion vulnerability that could lead to code execution and it received the track number CVE-2015-0336; it was plugged by the developer on March 12 with the release of version 17.0.0.134 and 13.0.0.277 (extended support) for Windows and Mac, and 11.2.202.451 on Linux.
Many users have not switched to the safer version of Flash
A couple of days ago, security researchers at Trend Micro observed the first instances of malicious activity relying on taking advantage of this glitch.
According to telemetry data from the security company, many users still have to update their version of Flash, as they are running the previous release.
“This exploit, detected as SWF_EXPLOIT.OJF, is being distributed to users via compromised websites, including one for an Internet Explorer repair tool and various Japanese pornographic sites,” Trend Micro threat analyst Peter Pi said in a blog post on Friday.
After being redirected to a landing page, the malicious code is loaded from a different website.
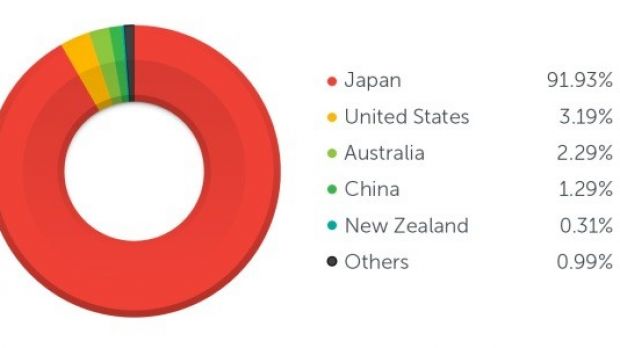
Users in Japan seem to be the target
Pinning this on Nuclear is based on the fact that the URLs used are similar to the ones seen in previous attacks with this browser-based tool; additionally, Pi says that the content on the landing page is consistent with the exploit kit.
Until now, the company recorded more than 8,700 users visiting the nefarious locations, the largest part of the IP addresses (91.93%) being located in Japan. Other countries observed are the United States, Australia, China and New Zealand, all accounting for less than 4% of the visits.
Cybercriminals updating their attack tools is not uncommon, but the interesting part is that they do it in a very short time after the vulnerability has been patched and disclosed, suggesting an organized group.
Users of Internet Explorer on Windows 8.x and above, and Google Chrome receive the latest Flash build automatically through their built-in update mechanisms. Flash has an auto-update feature and users that have it enabled are also delivered the new releases seamlessly.
 14 DAY TRIAL //
14 DAY TRIAL //