Local privilege escalation vulnerabilities have been found on versions 3.0 and 2.0 of North Korea’s own operating system, Red Star.
It is unclear how it happened, but an image of the OS was leaked on torrent websites, making possible its analysis by security researchers. This is most interesting since the Internet access is a commodity reserved only to a select few – 1,024 IP addresses are believed to be allocated for the entire country, which has about 24 million people.
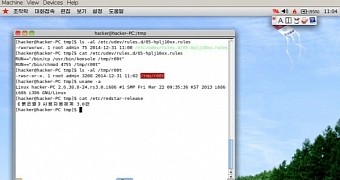
One researcher, posting under the name of Hacker Fantastic, took a peek and found that the software based on Linux contains security flaws that would allow an attacker complete control of the machine running the OS.
Hacker Fantastic discovered that the default configuration of the file permissions is insecure and permits execution of commands with administrator privileges.
“Red Star 3.0 desktop ships with a world-writeable udev rules ‘/etc/udev/rules.d/85-hplj10xx.rules’ which can be modified to include ‘RUN+=’ arguments executing commands as root by udev.d,” he wrote on Open Source Software Security (oss-sec) mailing list.
Udev is a device manager for the Linux kernel 2.6 that creates the necessary nodes for the devices connected to the machine. Upon unplugging the device, the manager removes the nodes previously created in the /dev directory.
Since the rules are world-writeable, an attacker that does not have root privileges could set up certain commands to be set up when a new device is connected.
 14 DAY TRIAL //
14 DAY TRIAL //