German-speaking users have been targeted by a new email spam campaign distributing a new version of Emotet banking Trojan that also compromises email accounts in order to self-spread.
The messages are written in German and generally claim to be bank communication in regard with an account statement problem. Other types of bait include fake phone bills or invoices from PayPal.
Most targeted banks are from Germany
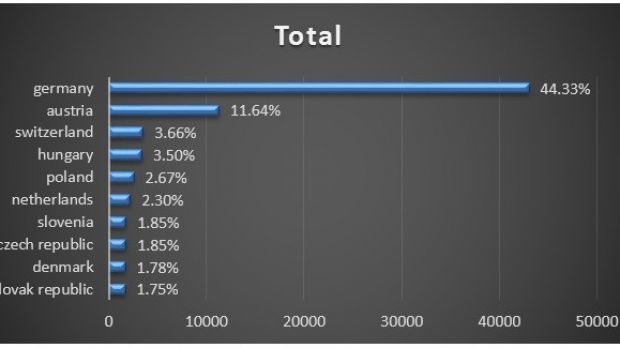
The most affected country is Germany, where more than 40,000 infections have been recorded in the past 30 days, followed by Austria and Switzerland, security researchers at Microsoft discovered.
Cybercriminals aim to gain access to accounts to several banks in Germany, but Wells Fargo and a financial institution in Austria have also been found on the list of targets in Emotet’s configuration file.
The fake financial document is archived and sent as an attachment. It poses as a PDF file that has a long name in order to hide that it is in fact an executable.
Researchers have found that the malware monitors client connections to financial institutions such as Flessabank, Bank1Saar, Berliner Bank, GE Capital, Sparda, CommerzBank, NorisBank, and Raiffeisen (Austria). However, accounts to telecom companies Vodafone and Telekom are also watched.
As soon as the victim loads the log-in page for the above mentioned locations, the malware automatically logs the credentials and sends them to a command and control (C&C) server.
Email log-ins are also at risk
To ensure a large number of victims, the author of the threat included a module that can steal the sign-in information for multiple local email clients. It can extract the username and password from Thunderbird, IncrediMail, Outlook (2000, 2002 and Express) and Eudora.
This data is delivered to the C&C, where it is used for further automatic distribution of the malicious emails.
The tactic ensures not only a wider reach to potential victims but also bypassing the traditional spam filters, since the messages come from legitimate addresses.
According to telemetry data from Microsoft, the new variant of Emotet was found in November, when the malicious email campaign was also most active.
By relying on compromised legitimate email accounts to spread the malware, the cybercriminals ensure that, even if a current operation is shut down, they can deploy another one at any time, using the harvested email credentials.
 14 DAY TRIAL //
14 DAY TRIAL //