A group of researchers has discovered that a specific type of LED light bulbs with network connectivity could be used by an attacker to capture and decrypt the credentials for the WiFi network from a distance of about 30 meters / 98 feet.
LIFX light bulbs are WiFi-enabled and can function in a network that is controlled through different wireless protocols using an app for mobile devices (iOS or Android). The user can thus control the light source by changing its color or intensity, programming it to turn on or off according to a predefined schedule.
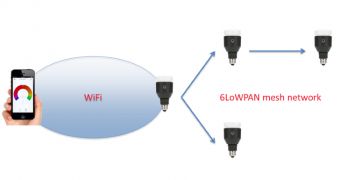
These light bulbs can be installed in a mesh network that is controlled by only one of them. In case this master LED bulb becomes unavailable, another one replaces it automatically.
Researchers at Context Information Security analyzed the way these smart light bulbs communicate with the network they’re connected to and discovered that there are three communication components in the LIFX bulb network: mobile device to bulb, bulb WiFi, and bulb mesh network communication.
LIFX bulbs rely on the 6LoWPAN wireless specification that is built on top of the IEE 802.15.4 standard, which specifies the media access control for low-rate wireless personal area networks.
By reversing the firmware of the light bulbs, the Context engineers observed that AES encryption was implemented for securing the communication through WiFi.
“AES, being a symmetric encryption cipher, requires both the encrypting party and the decrypting party to have access to the same pre-shared key. In a design such as the one employed by LIFX, this immediately raises alarm bells, implying that each device is issued with a constant global key.
“If the pre-shared key can be obtained from one device, it can be used to decrypt messages sent from all other devices using the same key. In this case, the key could be used to decrypt encrypted messages sent from any LIFX bulb,” they write in a blog post.
With the necessary knowledge, an attacker could be able to collect the encrypted WiFi credentials and decrypt them, without having to authenticate in any way or raising any alarm, from 30 meters / 98 feet away.
The vendor has been made aware of the glitch discovered during the research and responded promptly by issuing a firmware update, which encrypts all 6LoWPAN communications with a key derived from the WiFi credentials.
However, hacking the LIFX light bulbs is not an easy feat to pull, because the effort involved and the complexity of the task is not of ordinary levels.
Context researchers had to gain physical access to the micro-controllers embedded in the device in order to extract the firmware, identify the correct JTAG pins on the chips, use special equipment to issue commands to the chips, as well as reverse the extracted firmware.
Simon Walker from LIFX said that “prior to the patch, no one other than Context had exposed this vulnerability, most likely due to the complexity of the equipment and reverse engineering required.”
 14 DAY TRIAL //
14 DAY TRIAL //