Phishing attacks usually rely on a link planted in a cleverly designed email to trick users into handing over their personal details. However, over the past period, the number of phishing scams that leverage HTML attachments has increased considerably, Netcraft reports.
Experts have recently identified a phishing attack that targets Barclays customers.
The emails read something like this:
“Dear Barclays OnlineSM Customer:
Technical services of the Barclays Bank are carrying out a planned software maintenance. We earnestly ask you to visit the following attached form to start the procedure of confirmation of your online accounts.
To get started please download the form and follow the instructions on your screen.
NOTE: This instruction has been sent to all bank customers and is obligatory to follow. Thank you for your cooperation.
Best regards, Sean Gilchrist Digital Banking Director”
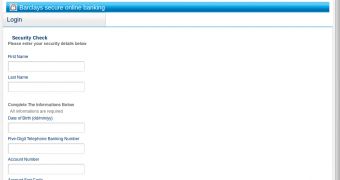
The attachment contains a form which requests recipients to enter their name, date of birth, five-digit telephone banking number, account number, and account sort code.
When the Update button is pressed, all the information is sent back to a remote web server via a POST request.
Experts believe that the crooks prefer to attach their malicious webpages directly to emails because this way it’s less likely that they’ll be blocked by anti-phishing systems. Furthermore, the attachment’s content is obfuscated to prevent security solutions from identifying it as a threat.
These types of schemes are called “drop site” phishing attacks because the only URL that’s involved is the one of the site where the stolen information is dropped.
“Drop sites can be difficult to recognise without the accompanying phishing mail. Usually, the 'drop' page just processes the victim's details and provides no indication as to its true nature. Some drop sites redirect to the target's real website,” Netcraft’s Vince Zarola explained.
“This merits suspicion for anti-phishing groups, but may not provide enough evidence for them to block the URL without the accompanying mail.”
Nevertheless, such attacks can be blocked by security solutions if they can detect the POST request that’s used to send the stolen information to the cybercriminals.
 14 DAY TRIAL //
14 DAY TRIAL //