Experts have developed a piece of Android malware that’s capable of recording the victim’s environment and reconstructing a 3D model based on the captured data.
Mobile security experts are constantly warning Android users to carefully analyze the permissions requested by an app before installing it. If it asks for more than it should, it may be a malicious piece of software that’s designed to steal information or even inflate the phone bill by sending out SMSs to premium rate numbers.
But what about apps that ask for permission to use the device’s camera? According to researchers from the Naval Surface Warfare Center in Crane, Indiana, and the Indiana University, allowing a program to gain control of your Android phone’s camera could be just as dangerous.
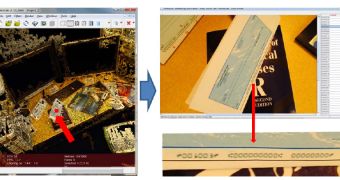
They’ve made a piece of visual malware called PlaceRaider that’s able to create an accurate 3D model of the user’s indoor environment by taking pictures and collecting data from other sensors.
The model created by PlaceRaider doesn’t only contain the big picture, but also the objects present in the environment, which could be anything from credit cards, financial documents, information from computer monitors and other sensitive data.
Robert empleman, Zahid Rahman, David Crandall and Apu Kapadia presented the “visual malware” in a paper called “PlaceRaider: Virtual Theft in Physical Spaces with Smartphones.”
PlaceRaider – which was designed to work on Android phones, for now at least – was tested on two subjects. The malware was able to create high-quality reconstructions of an indoor office by using “opportunistic data yields models with sufficient granularity.”
One noteworthy aspect is that during the tests, the subjects utilized the devices as they would normally do.
In order to make the data collection process as efficient as possible, PlaceRaider doesn’t record videos (although it could) because their size would make them difficult to transfer back to the command and control server.
Furthermore, not all the pictures taken by the application are sent back to the attacker, only the ones that could be useful. For this, the experts applied lightweight heuristics in order to identify and disregard uninformative images.
 14 DAY TRIAL //
14 DAY TRIAL //