Security researchers have found a vulnerability in the mobile email and web-based email systems of Prodigy, the Mexican telecoms company owned and operated by Telmex, that exposed the accounts of thousands of users.
In addition to the thousands of Prodigy customers whose accounts could have been compromised, millions more could be at risk because of the flaw, Tripwire experts who have analyzed the flaw warn.
“The hole has exposed at least several thousand email accounts, even enabling the indexing of email accounts and messages by Google and putting all Telmex customers who have an email on the Prodigy.net.mx and several other domains at risk,” Tripwire’s Ken Westin explained.
Users who have email accounts on the following domains are advised to immediately change their passwords: prodigy.net.mx, prodigymovil.com, prodigymedia.com, infinitummail.com, correoinfinitum.com, prodigywifi.com.mx, correoprodigy.com, infinitumzone.net and nombre.mitmx.net.
Those who utilize the same password for other accounts are recommended to change all of them.
“The security hole involved an application bug and server misconfiguration on a specific domain webmail2.prodigy.net.mx. The application serves as both the mobile email and webmail client application for Prodigy customers,” Westin noted.
This application didn’t have any proper authentication mechanism in place. Anyone could have accessed a customer’s email account simply by knowing the user ID parameter and the URL.
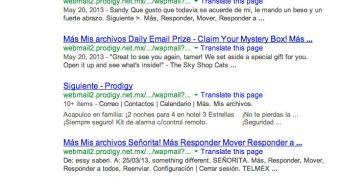
With the URL at hand, an attacker could have easily accessed email accounts. Even worse, these URLs and even the emails contained in the accounts were publicly available via Google.
Experts found over 3,000 pages of email account information indexed by Google.
The Prodigy mail system is believed to have been vulnerable since March 2010.
Fortunately, Google has removed the information from its systems. In addition, Telmex has addressed the issue after being notified.
However, that’s not the end of it. Westin warns that all logins to email accounts are done via unsecure connections. In addition, the server hosting the compromised application is running old and vulnerable versions of Apache and PHP.
 14 DAY TRIAL //
14 DAY TRIAL //