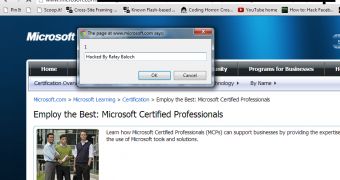
Microsoft has fixed a DOM-based cross-site scripting (XSS) vulnerability in the “Learning” section of microsoft.com after being notified by independent security researcher Rafay Baloch. The expert has provided us with a screenshot to demonstrate the existence of the security hole.
“The vulnerability I found is a DOM based XSS vulnerability. It is a third type of XSS also known as ‘type-0 XSS.’ Unlike other two types of XSS (Persistent and Non-Persistent), this type of XSS occurs because of modifying the DOM (Document Object Model) in the victims browser,” Baloch told Softpedia in an email.
He revealed that DOM-based flaws could be used for the same purposes as the other types of XSS vulnerabilities, including phishing, session hijacking, and stealing cookies. However, in this case, the attack method is different.
“I am not a fan of tools. I found it by injecting my payload manually. I feel that I can find bugs faster by going manually rather than using fancy tools, though there are tools like Dominator and Ra.2 making it easy for you to find DOM-XSS. I use them for verification,” he said regarding the methods he utilized to find the flaw.
He discovered the security hole on November 1 and reported it to Microsoft. By November 8, the Redmond company managed to review and address the issue with an online services update.
This isn’t the first time that the researcher finds security holes in Microsoft services. He is listed in Microsoft’s Online Researcher Acknowledgement page for October and because he found this DOM XSS, his name will appear in the November section as well.
In October, the expert’s work was acknowledged by security firm ESET, after he helped them in addressing a persistent XSS issue and an SQL Injection vulnerability on their Taiwan website.
 14 DAY TRIAL //
14 DAY TRIAL //