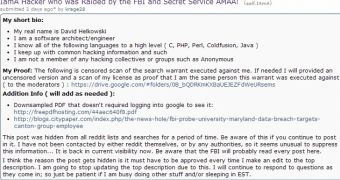
David Helkowski, a software engineer who got raided by the FBI and the Secret Service after hacking into the systems of the University of Maryland, has decided to share his story on Reddit.
The expert had found a vulnerability in the University of Maryland’s systems while working for Canton Group, a software company contracted by the university. He reported the vulnerability, which could have allegedly been leveraged to gain access to a lot of sensitive information.
However, after his reports were ignored, he decided to take matter into his own hands. He exploited the vulnerability from his home computer and downloaded a small number of information records, which he anonymously posted on Pastebin on March 15.
He used a VPN to protect his identity, yet, shortly after, he returned home from dinner to find his house being raided by FBI and Secret Service agents.
Since he claims he didn’t mean to cause any harm, and since his wife witnessed the entire raid, Helkowski decided to fully cooperate with authorities in their investigation. He even handed over the password for his system encryption and his Keepass password.
The man says no charges have been brought against him so far, but he no longer works for the Canton Group.
Although he tried to cover his tracks when he hacked into the university’s systems, he did share his plans with some people, including on a Steam chat, which might explain how law enforcement tracked him down so fast.
The FBI appeared to have a printout of the Steam chat log, which Helkowski believes was obtained directly from Steam or from someone in the chatroom. His friends and even his parents were questioned by authorities before the raid.
Helkowski says he might also be a suspect in the recent data breach in which the details of hundreds of thousands of individuals have been stolen. He claims to have gained more access than the cybercriminals who stole data from the organization, but he says he didn’t do “anything bad with that information or access.”
However, in a statement they published regarding the man’s case last month, University of Maryland representatives said the two breaches were unrelated.
“The FBI has informed the University that the intrusion resulted in no public release of any information and no damage to the institution, except for the release of personal data of one senior University official, who has been notified. We are unable to comment further on the intrusion at this time. This matter is unrelated to the data breach of February 18, 2014,” said Interim Vice President and Chief Information Officer Ann G. Wylie.
 14 DAY TRIAL //
14 DAY TRIAL //