An undocumented function in LNK shortcut file type is employed by Janicab, a Trojan that infects Windows and Mac systems alike, to pass command line arguments that are not visible to Windows’s file manager.
Janicab has been around for about two years, and it relies on Python and VBScripts to infect machines running the two operating systems. Its infection method has been deemed at the time as being quite interesting.
RLO and outsourced IP addresses for C&C servers
The malware used THE RLO (right-to-left override) technique, which resorts to a special Unicode character for languages where text is written right to left. It can be inserted anywhere in a text string, marking the beginning of the reversed writing.
This method is used in files with a double extension to make them appear as harmless DOC or PDF data, when in fact they are executables.
Janicab’s covert actions also include getting the addresses for the command and control (C&C) servers from third-party online sources, such as comments left for different YouTube videos.
The IPs are obfuscated via an algorithm that translates seemingly random numbers that have the pattern “our (.*)th psy anniversary” into the appropriate addresses. This tactic has been noted in previous versions of the malware.
Invisible commands, anti-analysis routines mark Janicab's evolution
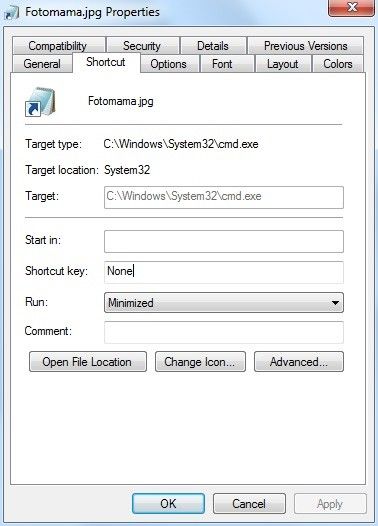
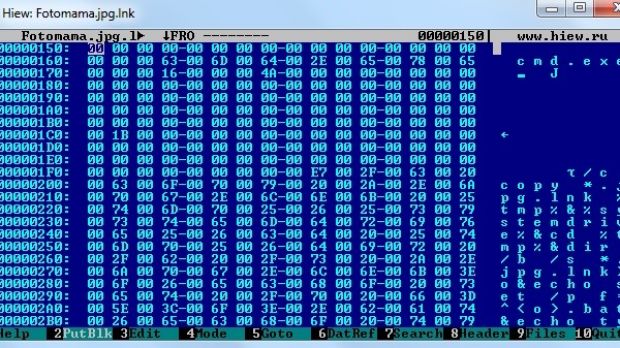
Security researchers at F-Secure discovered that a variant of Janicab for Windows delivered as a LNK file includes invisible shell commands enumerated in a string using the “&-” operator.
In the example provided by the researchers, the malware tries to pass as a shortcut for a JPG image, but the target location points to Command Prompt (cmd.exe), where the malicious commands are executed.
A malicious script encoded with Microsoft Script Encoder is appended at the end of the LNK file; it contains the instructions for dropping decoy files in order to quash suspicions when the user launches the shortcut.
The evolution of Janicab is also marked by the use of “snapIt.exe,” an application designed for capturing desktop screenshots.
Additionally, the variant found by F-Secure integrates anti-analysis routines that check if the malware is run in a virtual machine (VirtualBox, Parallels and VMWare) or a system intended for analyzing threats by verifying the presence of processes belonging to process managers, network analyzers, debugging and startup tools.
 14 DAY TRIAL //
14 DAY TRIAL //