Another incident involving digital certificates has been discovered. In this situation a piece of malware has been found to be signed by a certificate stolen from a government institution in Malaysia.
F-Secure's Mikko Hypponen reports that even though these situations are rare, they're not quite uncommon.
“It's not that common to find a signed copy of malware. It's even rarer that it's signed with an official key belonging to a government,” Hypponen reveals.
Cybercriminals will steal or even create themselves certificates which will make a malicious software seem more trustworthy in the eyes of the operating system and even the security solutions.
While unsigned applications can raise a lot of flags, signed applications, especially those that benefit from the signature of legitimate institutions, will be treated like a harmless element.
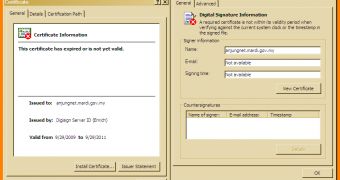
In this particular case, a malicious PDF file was discovered as being signed by anjungnet.mardi.gov.my which actually belonged to the Malaysian Agricultural Research and Development Institute. Malaysian authorities report that the certificate used to validate the malevolent file was stolen “some time ago.”
“The malware itself has been spread via malicious PDF files that drop it after exploiting Adobe Reader 8. The malware downloads additional malicious components from a server called worldnewsmagazines.org. Some of those components are also signed, although this time by an entity called www.esupplychain.com.tw,” Hypponen said.
The trojan was identified as Trojan-Downloader:W32/Agent.DTIW but fortunately, the certificate that validated it expired in September, which means it won't have the upper hand against security products any more.
In the recent period we've seen a lot of situations where cybercriminals hacked CAs to steal certificates that they can later use in malicious operations. In Malaysia, DigiCert Sbn. Bhd was discovered issuing 22 weak certificates, while in the Netherlands KPN stopped releasing them after discovering a DDoS tool on one of their servers which may have been there for about four years.
 14 DAY TRIAL //
14 DAY TRIAL //