A message circulating on Facebook promises access to a private video of actress Emma Watson but it delivers an army of Trojans that pilfer sensitive information from the gullible user.
The scam begins like a regular online survey deceit would on Facebook: the potential victim receives the message with the irresistible lure and is taken outside the social networking environment to play the alleged video.
Signs of the deceit are obvious
To make the campaign more credible, users are directed to a fake version of YouTube claiming to host the video under the account of a member of the Anonymous hacker group.
The fact that YouTube is allegedly used as the video sharing platform alone should ring some alert bells, since the service curates improper content both automatically and manually.
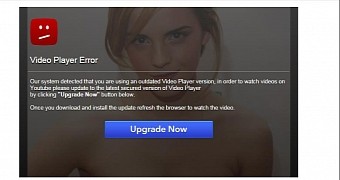
If this does not sound the alarm and the user proceeds, they are asked to update the video player version in order to watch the alleged adult content footage featuring Emma Watson.
Researchers at Bitdefender analyzed the downloaded file purporting to be an update for Flash Player and discovered that it was actually a Trojan designed to change the web browser configuration and prevent access to the list of extensions, Facebook activity and settings.
The Trojan can hijack Facebook session
The malware is identified as Trojan.JS.Facebook.A and drops malicious items in the installation folder of Internet Explorer; it can also steal the anti-CSRF (Cross-Site Request Forgery) token, permitting an attacker to hijack an authenticated Facebook session and make changes as if they were the user.
Bitdefender experts observed that the malicious extension can connect to a command and control (C&C) server, use scripts to access code from other websites and gain control over the activity on Facebook (post comments, follow pages).
It appears that the cyber gang behind this campaign tries to get the most out of it before it is blocked and seeks monetization through online surveys, too. The bad links perform redirects to localized surveys.
“This makes the scam more credible, as users can fill in the surveys in their own language,” says Bitdefender.
Even if this type of scam may seem harmless, personal information is requested when trying to complete a survey, which is generally presented as another hoop to jump through in order to watch the alleged video.
Judging by recent events, the current campaign preys on the massive leak of celebrity photos that started at the beginning of September.
 14 DAY TRIAL //
14 DAY TRIAL //