Inside the website of North Korea’s news service, KCNA, lurks malware pretending to be an update for old versions of Adobe Flash Player.
A security researcher analyzed the source code of the Korean Central News Agency (KCNA) website and discovered a suspicious file at the root of the site’s directory, “kcna.user.exploit.exploit.kcmsf” that contained JavaScript code responsible for downloading an archived executable for Flash Player 10.
Website runs on old code
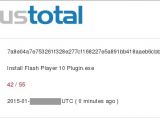
A security enthusiast writing at InfoSecOtter fed the executable file to the antivirus engines on VirusTotal, where most of the products (42 out of 55) marked it as malicious and indicated that it was a malware dropper.
ArsTechnica performed its own investigation and determined that the fake Flash update was created in December 2012, which corresponds to most of the code of the website.
They also found a JavaScript whose function was to check the Flash versions supported by the web browsers of the visitors. It appears that at the moment it was still checking for WebTV clients.
Watering hole attack possible
One interesting thing discovered by ArsTechnica is the fact that the dropper file is present in the code of all pages, and it is also readily available, but no string was found that calls for the variable holding the file’s location.
“However, the site has a significant amount of Ajax and jQuery-based dynamic code, some of which could be used to call the variable to launch the download for specific cases - for example, from specific stories in KCNA's home-grown content management system for site visitors with specific browsers,” Sean Gallagher explains.
This would suggest a “watering hole” type of attack, which targets visitors interested in certain news stories.
At the moment, there are no details about what the malware does in particular or the address it communicates to, but InfoSecOtter promised a new post with information taken from the runtime code on the debugger, modifications made to the compromised system, and insights from packet traffic analysis, which should reveal the location at the other end.
 14 DAY TRIAL //
14 DAY TRIAL //