In 55 days, KorBanker malware designed to steal banking information from Android devices managed to collect more than 10,000 text messages from 96 infected smartphones.
The banking malware is not new, its activity being monitored by security researchers since September 2013.
It reaches the devices of the users by masquerading as the Google Play app, and after installation it looks for the presence of mobile banking apps from a set of targeted banks.
If any such apps are detected, they are automatically deleted and replaced with a fake version; then it waits for text messages with two-factor authentication (2FA) for logging into accounts of targeted banks.
All the information in the spoofed banking apps and the SMS is then sent to a command and control (C&C) server.
“The [C&C] server for KorBanker is known to respond back with a HTTP 404 error page, even though the server is up and running. A custom 404 error page leads the average user to believe the server is no longer functional,” says Hitesh Dharmdasani, mobile threat researcher at FireEye.
Dharmdasani managed to obtain a database with information exfiltrated from 96 compromised devices and found that communication via SMS with more than 3,500 users had been uploaded to the C&C.
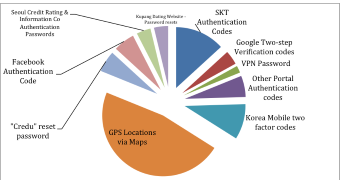
According to FireEye data, the country code in the phone numbers indicates that most of the infected Androids are located in Korea.
The type of information collected by the attacker includes two-step verification codes from services from Google and Facebook as well as passwords for VPN services. Moreover, location sharing info is also exposed through texts from other online products.
Given the sensitivity of the information syphoned, KorBanker for Android poses a great risk not just to the regular user, but also to businesses, since access to their networks can be gained based on the intelligence collected from an infected device.
The longevity of the malware, together with additional details discovered by FireEye, suggests that the threat is part of a large operation with multiple distribution points.
Recently, the company has detected a spike in activity, identifying more than 1,700 devices since August 1.
“Our research shows us real-world evidence that mobile malware can indeed be part of a larger operation through which cyber criminals gather victim’s information. Adding to the already complex threat landscape, it remains to be seen how multi-vector threats, including mobile malware, will evolve in the future,” concludes the researcher.
 14 DAY TRIAL //
14 DAY TRIAL //