IT security giant Kaspersky has started publishing its security bulletins for 2013. One of them focuses on the threats that target corporations.
The report covers attackers’ motives, organizations targeted over the past year, intrusion techniques, attack preparation methods, technologies, the type of information that gets stolen, and the activities of cyber mercenaries.
According to Kaspersky, the number of serious cyberattacks has increased considerably over the past couple of years. In fact, a recent study has shown that 91% of companies suffered at least one attack over a 12-month period. Furthermore, 9% have reported being the victims of a targeted attack.
As far as motives are concerned, one of the main reasons for which organizations are targeted by cybercriminals is sensitive information. Other motives include sabotage, money theft, causing damage to a company’s reputation, and causing financial losses – usually with the aid of DDOS attacks.
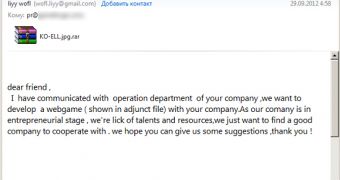
There are several intrusion techniques used by cybercriminals to breach an organization. However, one of the weakest links in an organization’s defense systems are its employees. Numerous companies have been breached after their employees opened malicious attachments or clicked on links that pointed to the hackers’ websites.
A number of campaigns have stood out in 2013, such as Red October, Kimsuky and Winnti. Each of them has leveraged some interesting technologies to achieve its goals.
When it comes to cyber mercenaries, these are well-organized groups of highly skilled hackers that can be hired by private companies and even government agencies to conduct targeted attacks. Unlike other cybercriminals, mercenaries don’t steal any type of information, but only one they’re interested in.
Additional details are available in Kaspersy’s security bulletin. You can also check out the video in which Vitaly Kamluk, principal security researcher at Kaspersky’s Global Research & Analysis Team, details corporate threats:
 14 DAY TRIAL //
14 DAY TRIAL // 