A detailed XSS filter architecture and implementation article has been published on the Security Vulnerability Research & Defense blog. The main goal of the XSS filter integrated in IE8 is to prevent exploitation of cross-site scripting vulnerabilities without breaking the web.
Cross-site scripting (XSS) is a type of vulnerability common to web applications, which allows injection of malicious code into a legitimate web page viewed by other users. Depending on the injected code, the results can have serious repercussions. According to MITRE, XSS Type-1 vulnerabilities rate among the most common on the internet, exceeding the buffer overflow types which came on first place for many years. The rise of XSS vulnerabilities prompted browser developers to implement serious security features. Microsoft's response is the XSS filter for Internet Explorer 8, which will be introduced in the Beta 2 version.
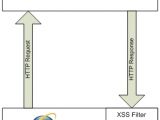
The XSS filter was built with several considerations: to reduce disruption of legit data/content to a minimum, to reduce the possibility of subverting it without compromising the performance, and to be as fast as possible. In order to intercept requests and replies in the browser, the filter was built directly into the rendering engine of IE8 (MSHTML), while initially it was implemented as a MIME filter.
In order to not slow down browsing, the filter only comes into action when a cross-site navigation is encountered or when the source of a rendered element can't be determined. The possibility of disabling the filter for certain zones like the Intranet is also available.
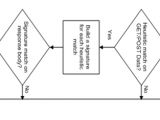
The filter operates in two steps. First, it scans the GET/POST data using heuristics in order to identify XSS attacks. If a match is found, a signature is built to identify the malicious markup. The signature is then applied to the HTTP response, and the identified markup is being modified and blocked while keeping the rest of the page intact. At the core of the heuristics sets and signatures are regular expressions. Each heuristics contains a list of safe characters. The rest of the characters that are un-safe will be replaced with a neutering character, which will render the markup inactive.
Even so, the XSS filter is not perfect. Some compromises had to be made in order to achieve a good balance between security, compatibility and performance, and not break web sites. While it protects from the general and most common forms of XSS attacks, some specific attack scenarios, like the "Referrer" based injection, are still not covered. David Ross, Security Software Engineer on the SWI team notes that "as time goes on we will continue to enhance the XSS Filter to maximize its effectiveness, however we will not compromise web site compatibility in the process."
 14 DAY TRIAL //
14 DAY TRIAL //