The United States Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) has revealed that researchers Billy Rios and Terry McCorkle of Cylance have identified critical vulnerabilities in around 300 medical devices from around 40 vendors.
The experts have found that the devices in question have hard-coded passwords that can allow an attacker to modify critical settings or the devices’ firmware.
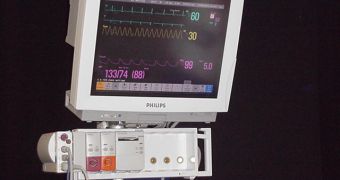
The list of impacted items includes surgical and anesthesia devices, ventilators, drug infusion pumps, external defibrillators, patient monitors, and laboratory and analysis equipment.
The hard-coded passwords are in place so that technicians can access the devices. However, since the passwords are easily obtainable, there’s nothing to stop cybercriminals from abusing them.
Although there’s no evidence that any of the vulnerabilities have been exploited, the US Food and Drug Administration (FDA) and ICS-CERT have notified the affected vendors and asked them to “identify specific mitigations.”
The FDA has released an advisory of its own, providing advice for both device manufacturers and health care facilities.
“The FDA expects medical device manufacturers to take appropriate steps to limit the opportunities for unauthorized access to medical devices,” the FDA wrote.
“Specifically, we recommend that manufacturers review their cybersecurity practices and policies to assure that appropriate safeguards are in place to prevent unauthorized access or modification to their medical devices or compromise of the security of the hospital network that may be connected to the device.”
Until this situation is addressed, the FDA recommends health care facilities that they restrict unauthorized access to the network and networked medical devices, and make sure that appropriate protection software is in place.
Organizations are also advised to monitor network activity for unauthorized use, and to perform routine and periodic evaluations of individual network components.
 14 DAY TRIAL //
14 DAY TRIAL //