A large number of the world’s top websites have been impacted by the OpenSSL vulnerability dubbed the “Heartbleed bug.” Fortunately, many organizations have already patched their installations.
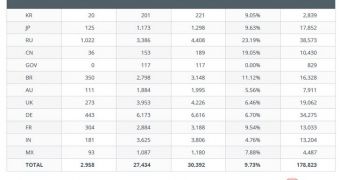
According to Trend Micro, less than 10% of websites are still vulnerable. The US government has ensured that all its 117 .gov websites are patched. In fact, .gov is the only top-level domain (TLD) with 0 vulnerable websites.
Domains for Australia, the United Kingdom, Germany and India are also mostly patched up. There still are many vulnerable sites in Russia, China and Brazil, experts have determined.
“Overall, the numbers leave room for optimism when it comes to addressing Heartbleed. Most system administrators have paid attention to the warnings and patched their servers accordingly,” Trend Micro Senior Threat Researcher Maxim Goncharov explained in a blog post.
“The question is now whether the remaining 10% of vulnerable domains will be patched sooner rather than later, or if we will be stuck with a non-trivial portion of the Internet that will be left at risk.”
The fact that most organizations have patched their OpenSSL installations is also confirmed by Distil Networks. Earlier this week, the company reported that 84% of the top 10,000 global websites had applied the patch to fix the Heartbleed bug.
Distil, which specializes in bot protection, has developed a bot capable of checking the dates on which SSL certificates have been issued. Companies must re-issue their digital certificates because they could have been compromised by hackers exploiting the Heartbleed vulnerability.
For the time being, Distil says that 9% have issued new certificates, but 15% haven’t done so. For the other 76%, the results are inconclusive.
Several tools have been released to help organizations determine if their installations are vulnerable. Trend Micro has also developed a couple of tools to help users determine if the websites they’re visiting or the Android applications they’re using are susceptible to Heartbleed attacks.
The problem with Heartbleed attacks is that they’re difficult to detect. That’s why many of the impacted companies have decided to change all their digital certificates and advise their customers to change their passwords as a precaution.
Of course, changing passwords was the first piece of advice given by experts after the world learned of Heartbleed. However, as many have highlighted, changing passwords would have been ineffective if the service in question hadn’t patched its OpenSSL installation.
In the meantime, Google, Facebook, Microsoft, Amazon and other major players have joined forces for a Linux Foundation project called the Core Infrastructure Initiative. The goal is to ensure that we don’t see another Heartbleed any time soon.
 14 DAY TRIAL //
14 DAY TRIAL //