On Tuesday, Pakistani hacker H4x0r HuSsY breached and defaced the official forum of the openSUSE Linux distro. The attacker claims to have exploited a vBulletin zero-day to upload a shell and gain access to the forum database.
The hacker has told The Hacker News that the zero-day is his own. It allegedly allows him to read and write any file on the forum server without root privileges. He hasn’t provided any additional details.
Meanwhile, OpenSuSE has shut down its forum. The organization’s representatives say they’ve taken this decision because there’s no workaround and no fixes for the exploit. vBulletin has not made any comments on the issue.
So what information has the hacker compromised? Initially, openSUSE noted that user accounts couldn’t have been compromised because of the authentication system they’re utilizing.
“Credentials for your openSUSE login are not saved in our application databases as we use a single-sign-on system (Access Manager from NetIQ) for all our services. This is a completely separate system and it has not been compromised by this crack,” openSUSE stated.
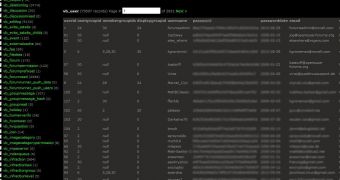
On the other hand, the hacker has provided The Hacker News with an image (see screenshot) which shows that he has gained access to what appears to be encrypted passwords. openSUSE says there’s an explanation for that.
“What the cracker reported as compromised passwords were indeed random, automatically set strings that are in no way connected to your real password,” they noted.
However, they do admit that the Pakistani hacker has obtained user email addresses.
This isn’t the first time when unconfirmed reports of a vBulletin zero-day surface. Back in November, hackers of Inject0r Team claimed to have breached MacRumors and the vBulletin.org by exploiting a vBulletin zero-day vulnerability.
At the time, vBulletin representatives said they couldn’t find any evidence that the zero-day really existed.
 14 DAY TRIAL //
14 DAY TRIAL //