In the revelations about the Equation cyber-espionage group, Kaspersky published details about a module that can modify the firmware of mass storage devices on Windows machines, but there may be versions for Apple products, too.
Part of the EquationDrug platform, the module (nls_933w.dll) is designed to reprogram the firmware of storage units (HDD/SSD) from more than a dozen manufacturers and plant malware that would resist formatting or re-installation of the operating system.
Variants for iOS and OS X likely to be used
Achieving persistence at firmware level is highly worrisome because the victim would not be aware of the compromise (regular security products cannot detect it) and the only way to get rid of the infection would be to destroy the hard disk.
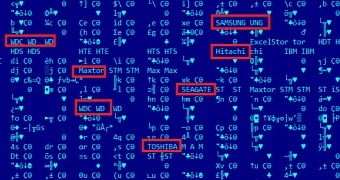
Among the vendors targeted by nls_933w.dll, Seagate, Western Digital, Toshiba, Hitachi, Maxtor, IBM, and Samsung are mentioned.
Security researchers from McAfee have analyzed a sample of the malicious module for Windows and said that there is evidence that variants for other platforms have also been created.
“The most recently discovered HDD/SSD firmware reprogramming modules were compiled starting in 2010. Both 32-bit and 64-bit versions of the plug-ins have been found. Although the analyzed samples target only Microsoft Windows systems, there are indications that versions also exist for Apple iOS and OS X systems,” the company said in a report on Monday.
Highly complex operation
The EquationDrug platform has been in use since 2003, but newer victims are attacked with a newer one, called GrayFish, which also includes firmware reprogramming modules.
After the targeted system is compromised with EquationDrug, nls_933w.dll takes care of altering the firmware so that it creates a hidden data storage space to host the payload. A different module ensures communication with the area and allows loading the malware piece.
Changing the firmware is done using a set of commands that are not available to the public and are specific for each vendor. However, some of them are shared by multiple manufacturers and these are used where possible, McAfee says.
Equation Group is the most advanced threat actor discovered to date. It managed to access secret documentation and to reprogram the firmware of storage drives from a large number of vendors, a feat considered close to impossible by many reverse engineers.
 14 DAY TRIAL //
14 DAY TRIAL //