Cybercriminals are using the Cutwail spam botnet to send out fake T-Mobile and Swisscom notifications in an effort to spread a piece of malware.
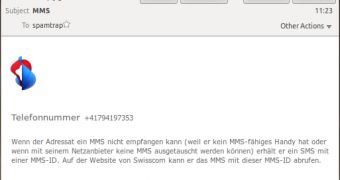
The notifications that target Swiss Internet users inform recipients that in case they receive MMS messages, but their phones are unable to display them, they will receive a code via SMS which they have to enter on the Swisscom site.
While the email looks legitimate, especially since its body has been copied from the official Swisscom site, the file attached to it is an executable which unleashes a Trojan that’s designed to avoid running in virtual machine environments.
Once it’s executed, the threat starts communicating with a command and control server located on a Russian domain registered in December 2012.
In the attacks that target German internauts, the bogus messages appear to come from T-Mobile. They’re slightly different than the ones that leverage Swisscom’s name, but the malware they distribute is the same.
The good news is that spam filters that check the sender’s IP address against Spamhaus’ ZEN will likely block the malicious emails. Additionally, spam filters configured to check the sending domain’s SPF record will also block out the messages because Swisscom has published a SPF record for Swisscom.ch.
Abuse.ch experts, who have closely investigated this Cutwail campaign, advise users to ensure that all their incoming emails are compared against Spamhaus ZEN, and enable SPF checking on their spam filters.
Also, since the malicious files attached to these emails look something like MMS-XXXXXXXX.JPEG.exe, it would be useful to make sure that file extensions are visible.
Finally, the IP addresses and the domains associated with the botnet’s command and control servers should be blocked.
A technical analysis of the spam campaign made by Abuse.ch is available here.
 14 DAY TRIAL //
14 DAY TRIAL //