A new report giving information about the latest trends in vulnerabilities leveraged by cybercriminals places Adobe’s Flash Player browser plug-in in top spot as far as zero-day attacks are concerned.
Bromium, a firm providing endpoint security solutions, released its statistics regarding abuse of vulnerabilities in software products like Microsoft Internet Explorer, Mozilla Firefox, Google Chrome, Java, Adobe Flash, Adobe Reader, and Microsoft Office.
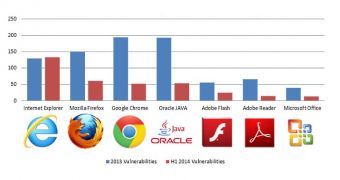
According to the report, Microsoft’s web browser was the most patched since the beginning of the year and also the most exploited. However, the researchers note that security patches for version 11 of the product were delivered at a fast rate, when compared to the previous revisions.
As far as leveraging zero-days in browser plug-ins is concerned, Adobe’s Flash Player came out uncontested as the most exploited.
Attackers dug deep in the features released last year and managed to find flaws in the ActionScript Virtual Machine ASVM implementation, which they could take advantage of through “ActionScript Spray” methods in order to be able to run arbitrary code on an affected system.
Bromium reports that non-ASLR (Address Space Layout Randomization) libraries were still the weak spot permitting malware authors to bypass the security measures in the operating system.
These are the most prominent exploitation techniques, but other breach methods taking advantage of zero-day flaws in the case of Adobe Flash Player have also been observed.
With Internet Explorer, the report points out that most of the “memory corruption exploits now use de facto ROP (Return Oriented Programming) techniques for bypassing the default Operating System security mechanisms (ASLR, DEP).”
Bromium documented three severe security glitches that bypassed DEP (Data Execution Prevention) and ASLR, which were used in live attacks and exploited non-ASLR libraries of Flash Player (CVE-2014-0497), JRE 1.6 and 1.7, and MS Office 2007 and 2010 (CVE-2014-0502), and one security glitch relying on dynamic ROP generation based on ActionScript Spray (CVE-2014-0515).
An interesting detail is the fact that in the first half of 2014 there was no report of zero-day vulnerabilities in Java.
“2010-2013 were clearly the years of Java exploits. Since then a lot of things have changed: old versions of JRE are blocked in the browser by default, Java applets now require explicit activation from users so this attack vector becomes harder and harder to leverage. In response to ever increasing defenses deployed by security vendors and software developers attackers switched to other popular plugins,” say Bromium researchers.
The conclusion of the Bromium report is that the most popular targets for exploitation in the first half of this year are Internet Explorer and Adobe Flash Player.
 14 DAY TRIAL //
14 DAY TRIAL //