Duqu and Stuxnet, currently known as the most complex pieces of malware ever built, are joined by another malicious element that’s been spotted by experts as targeting networks from the Middle East. Security researchers have analyzed the threat and dubbed it Flame.
A number of renowned companies have released their findings, including Symantec, CrySys, Kaspersky and even Iran’s National CERT, all cataloging the new threat as being highly dangerous.
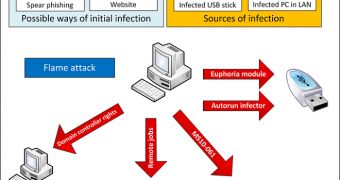
Each firm dubbed the attack and the malware that powers it differently. For instance, Symantec baptized it Flamer, CrySys called it Skywiper, and Kasperky name it Flame, which is how we’ll refer to it in this article.
Symantec has found that Flame is most likely developed not by a single individual, but by a cybercriminal organization with clear objectives and which possesses considerable financial resources. It’s believed that the threat’s primary targets are located in Eastern Europe and the Middle East, more precisely countries such as Iran, Lebanon, Syria and Israel.
While Flame’s purpose is information and data theft, initial analysis shows that not all the victims are targeted for the same reasons, mainly because not all of them are associated with a single industry.
According to Kaspersky, Flame can’t be cataloged as being a worm or a backdoor. Instead, it’s more like a “sophisticated attack toolkit” that is a backdoor and a Trojan with worm-like capabilities.
When it comes to the malware’s degree of sophistication, experts have discovered that when fully deployed, it totals up to around 20 megabytes in size, consisting of many libraries and modules. This makes the threat fairly difficult to analyze in comparison to other malevolent elements.
Regarding its features, it has been found that it cannot only record audio data and log keystrokes, but it can also take screenshots and leverage Bluetooth connections in order to collect information from nearby devices.
As with Duqu and Stuxnet, there are a lot of unknown aspects. It’s believed that Flame has been created sometime in 2010, but some of the files date as far back as 1992, 1994, and 1995.
Also, the code doesn’t provide any hints to the identity of its creators, but Flame has been named as a state-sponsored threat.
Bitdefender has already released a Flame removal tool. Details and download links are available here.
 14 DAY TRIAL //
14 DAY TRIAL //