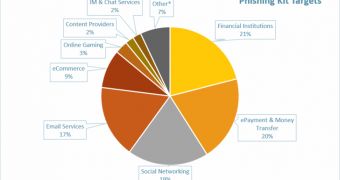
A new study from a security firm reveals that financial institutions represent 21% of the targets of phishing kits, followed closely by money transfer services.
PhishLabs examined a total of 9,000 phishing kits and their variants gathered from various online sources and determined the services that are most prone to phishing attacks.
Phishing kits consist in content (web pages, images, scripts, and webserver code) that can be installed on a server with the purpose of collecting sensitive details from a victim; these bundles require minimum configuration and most of the times they are available for a fee.
The malicious components were found not just on compromised servers and illegal machines but also on underground forums, file sharing services and even blogs.
The results of the study showed that the targets also include the social networks (19%), email services (17%), e-commerce products (9%), online gaming (3%), IM services and content providers, sharing a 2% risk each.
Keeping up with the trends in cybercriminal activity requires constant checking of the threats currently available on the market. This enables the security companies to elaborate new, more efficient approaches in fighting the digital criminal activity.
Don Jackson, Director of PhishLabs Threat Intelligence, says that “some of the kits analyzed were obviously intended for widespread, indiscriminate distribution. Others were more targeted or customized for private use, and some appeared to be hand-crafted for a particular purpose or an exclusive target.”
Among the findings, there were four kits designed for the Bitcoin community; two of them emulated different exchange services, one targeted a payment service and another a community forum.
The distribution methods for the phishing links are diverse and apart from malicious search engine optimization in order to rank high in the results, the cyber crooks also reach their victims through spam emails, short message texts on smartphones or posts on social networks.
In a recent report about phishing tactics in the Steam community, cybercriminals resort to all sorts of tricks to get their hands on the user’s login credentials and to bypass two-factor authentication security measures.
Once they have the keys to the account, there is no stopping them from selling the valuable available item. Some Steam accounts are worth thousands of dollars.
The PhishLabs report concludes that crooks invest a lot in creating and distributing the phishing kits and a good deal of them have the possibility to monetize credentials for social networking and email services; but, more importantly, “cybercriminals are able to attack a very wide range of organizations without needing to create their own phishing content.”
 14 DAY TRIAL //
14 DAY TRIAL //