Unknown actors deploying a targeted attack against a financial institution in Asia managed to run the operation under the radar for three months, despite relying on malware that lacked the complexity researchers are used to see in such cases.
The time of intrusion appears to be January, based on file creation dates, and planting the malicious software was possible through spear-phishing, experts from Cyphort say.
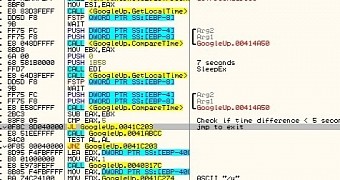
Malware detects sandbox sleep acceleration
Following an analysis of the threats, researchers found that all samples were unpacked, except for one, and that the code sections resembled those of normal files, which would allow it to bypass heuristics-based antivirus detection.
In at least one case, Cyphort’s assessment determined that a threat could defeat a sandbox by lying dormant for a period of time. Although analysis tools include a function that accelerates the passage of time, to see the malware in action, this sample was able to check if such a technique was employed.
A total of six samples have been found by the researchers, including backdoors and infostealers, that allowed the attacker to gather sensitive information and have access to the compromised systems.
Attackers had strong control over the systems
Apart from logging the activity of the computer (screenshots, capturing mouse and keyboard events), some of the threats could also enumerate the local and network drives, open remote access shells, download and execute programs, terminate running processes, gather details about installed security products or search for the presence of certain security solutions.
Additionally, the espionage component of one of the malware pieces included video and sound capture capabilities, stealing clipboard content, erasing traces useful in forensic activity, creating new users or rebooting the compromised system, as well as displaying pop-ups and removing its traces from the machine.
No single security solution is effective against all malware
According to Cyphort, the command and control (C&C) servers used for communication are registered in Korea, although the records do not seem genuine.
In a blog post published on Tuesday, the company concludes that malware does not need to be advanced to be effective. In this case, three months of stealth offered the attacker plenty of operation time, yielding passwords and valuable insight into the targeted organization.
Despite antivirus solutions remaining an important part of a company’s security, the numerous techniques employed by attackers make it clear that a single product cannot deal with all threats.
 14 DAY TRIAL //
14 DAY TRIAL //