Expecting something from the Royal Mail? Beware! A malicious email purporting to come from the organization might land in your inbox these days.
Dynamoo’s Blog has investigated the spam campaign. One of our readers has also reported receiving such an email, which indicates that a lot of people are getting the malicious notifications.
The fake messages purport to come from the Royal Mail and they carry the subject line “Royal Mail Shipping Advisory, Thu, 27 Feb 2014.” Of course, the date will probably be different in the upcoming days.
The emails read something like this:
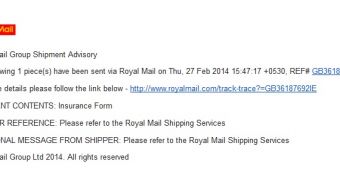
“Royal Mail Group Shipment Advisory
The following 1 piece(s) have been sent via Royal Mail on Thu, 27 Feb 2014 15:47:17 +0530, REF# GB36187692IE
For more details please follow the link below - http://www.royalmail.com/track-trace?=GB36187692IE
SHIPMENT CONTENTS: Insurance Form
SHIPPER REFERENCE: Please refer to the Royal Mail Shipping Services
ADDITIONAL MESSAGE FROM SHIPPER: Please refer to the Royal Mail Shipping Services
Royal Mail Group Ltd 2014. All rights reserved.”
The link appears to point to the Royal Mail website, but it doesn’t. Instead, it points to a website that hosts a page which triggers the execution of one or more malicious scripts.
According to Conrad Longmore, the payload is the Angler Exploit Kit. This exploit kit is designed to look for Java and Flash Player vulnerabilities on the targeted computer and leverages them in an effort to push malware. Back in November 2013, a known vulnerability in Microsoft Silverlight’s web browser plugin was added to the Angler Exploit Kit.
If you come across such emails, act with caution. Make sure the link really points to the Royal Mail website before clicking on it. If you place the mouse cursor over the link (without clicking on it), you can determine where it actually points to.
A different Royal Mail-themed spam run was making the rounds back in December 2013. At the time, recipients were tricked into opening a file attached to emails entitled “Mail – Lost / Missing package.”
“Royal Mail has detained your package for some reason (for example, lack of a proper invoice, bill of sale, or other documentation, a possible trademark violation, or if the package requires a formal entry) the RM International Mail Branch holding it will notify you of the reason for detention (in writing) and how you can get it released,” the emails read.
At the time, the malware was hidden inside a Zip file that appeared to contain a PDF document. When opened, a Trojan downloader was unleashed.
 14 DAY TRIAL //
14 DAY TRIAL //