Cybercriminals often sign their creations with digital certificates to make sure they're more effective in carrying out their malicious tasks. While in many cases the code-signing certificates are obtained legally, sometimes the attackers steal them from other companies.
Microsoft provides some interesting examples of malware signed with valid digital certificates. For instance, the fake antivirus family Rogue:Win32/FakePav, which had been inactive for over a year, resurfaced.
Its creators have apparently tricked at least a couple of certificate authorities (CAs) into issuing certificates. In such cases, the CAs are usually unaware that the certs will be utilized for malicious purposes.
Another example is the one of the fake antivirus known as Rogue:Win32/Winwebsec. In this case, cybercriminals have been using stolen certificates to sign a rogue security program called Antivirus Security Pro.
The attackers have used credentials stolen from at least 12 software developers from various countries, including the US, the Netherlands, Russia, Germany, Canada and the UK.
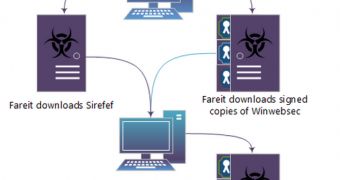
As far as information-stealing malware is concerned, Microsoft has found that there are several malware families that interact with each other.
The latest versions of the Trojan known as Fareit are capable of stealing not only passwords, but also digital certificates. Once it infects a computer, the threat downloads Sirefef and signed copies of Winwebsec. In turn, Winwebsec retrieves digitally signed copies of the threat called Ursnif.
“Cybercriminals and nation-backed operators have quickly learned that the best way to breach networks and get their hands on sensitive data and intellectual property is to make themselves appear as trusted entities within the environments and networks they infiltrate,” Venafi CEO Jeff Hudson has told Softpedia.
“The Win32/Winwebsec example is just another feather in the attackers’ cap, and, as Microsoft points out, new certificates are being stolen at an incredibly high rate,” he added.
The expert highlights the fact that stolen, spoofed or compromised certificates and cryptographic keys are a prefect vector for advanced, targeted attacks. That's because certificates can be used to sign not only code and malware, but also secure VPNs, authentication systems, applications, clouds and even mobile devices.
“Digital keys and certificates are the Internet equivalent of gold and we will continue to see the headlines riddled with similar attacks in the years to come because of the simple truth that we are losing the battle to identify and secure these incredibly valuable trust instruments that allow users to seamlessly infiltrate even the most secure security investments,” Hudson added.
Venafi’s CEO points to a recent Ponemon Institute study which shows that attacks leveraging compromised certificates and cryptographic keys could cost organizations as much as $35 million (€25 million) per incident.
While the average enterprise uses almost 18,000 such elements, 51% of those who took part in Ponemon’s study have admitted that they couldn’t identify the precise number of digital certificates and keys they had on their networks.
“Quite the smorgasbord for an attacker if the right steps aren’t taken to protect such a powerful and mission-critical capability. Organizations must implement a layered security solution that includes proper control of keys and certificates to ensure that all communications and transactions are secure and that networks remain protected from APT-style attacks,” he said.
 14 DAY TRIAL //
14 DAY TRIAL //