A dangerous scam has been found to circulate on Facebook, using more complex social engineering tactics to compel victims to install malicious software.
The scam uses a video lure, which is recommended by one of the victim’s Facebook friends through a regular post.
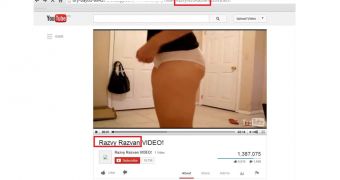
In most cases, this is enough of an incentive to click on the message, but some users may not fall for the trick when redirected to a malicious page asking them to update Flash Player in order to access the footage. As such, the crooks went as far as creating a fake YouTube page for the video that allegedly shows a woman undressing in front of a webcam.
The fake page looks like YouTube and shows an impressive number of viewers (almost 1.4 million) who also liked or disliked the clip. Catching wind of the deceit is easy if the address is checked, as it shows a different domain than the one used by Google’s video service.
According to Bitdefender, who analyzed the malicious campaign, the scammers created more than 20,000 unique URLs redirecting potential victims to dodgy websites.
The cybercrooks managed to get their hands on more than 60 bit.ly API keys that allow generation of shortened links, used in spreading the scam on Facebook; bit.ly has been notified by the abuse.
The fake Flash Player update is actually a Trojan that is detected by Bitdefender's computer protection software as Trojan.Agent.BDYV. Once run, a password-protected archive is dropped on the system along with a BAT file that proceeds to launch the executable by providing the necessary passcode for the decompression.
Because the malware can access data stored in the web browsers, “it tags 20 Facebook friends at a time and injects ad services into the page” to increase the lifespan of the scam, Bitdefender told us via email. Moreover, it appears that users cannot delete the posts that distribute the malicious redirects.
The security company says that the perpetrators may be from Albania, based on the analysis of the malicious code samples. Also, for writing the malware, they relied on an add-on framework, ensuring compatibility with multiple web browsers, Google Chrome and Mozilla Firefox included. The fake Flash update is being served in both these cases.
Crooks appear to be in the game of surveys, too; these are used to ask for sensitive details like the phone number, and a subscription to premium-rate short text message services is created.
Should the victim try to find the browser extension responsible for the rogue actions, the tab with the add-on may automatically close.
 14 DAY TRIAL //
14 DAY TRIAL //