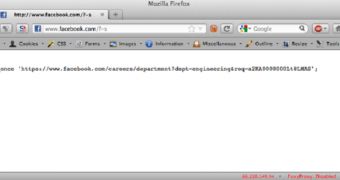
Update. Mr. Fuller was kind enough to clarify that this isn't actually a vulnerability in Facebook, but a clever way in which the company looks for security engineers. The "source code" was actually a link to a job application page.
Security expert Robber Fuller, also known as Mubix, has demonstrated that Facebook is vulnerable to the PHP-CGI flaw presented yesterday by security experts from De Eindbazen, at least as far as the source code disclosure part is concerned. Fuller, who is the main editor of Room362.com, posted a tweet in which he showed that if you write “facebook.com/?-s” the result is a piece of PHP source code, which normally you wouldn’t see when viewing the wepbage’s code from the browser.
Shortly after the details of the issue were made public, an exploit module of the PHP-CGI bug has been added to the Metasploit Framework, the project used by security professionals to identify security holes and verify vulnerability mitigations.
Besides allowing a remote attacker to disclose source code, the same vulnerability can be utilized to execute commands, but it’s uncertain at this time if the social media site is susceptible to this.
 14 DAY TRIAL //
14 DAY TRIAL //