Shortly after it released Firefox 16, Mozilla had to pull it back because a researcher found a vulnerability that could be leveraged by an attacker to access URLs or URL parameters of websites visited by the user.
Although it was initially believed that the flaw could be leveraged to access browsing history, Mozilla representatives told Ars Technica that “the flaw allowed access to the URL of windows or frames to which the attacker has a reference only—generally the ones that the attacker opened.”
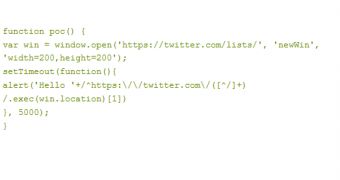
The researcher who uncovered the issue published a short proof-of-concept to demonstrate his findings and experts from security firm Imperva described how an attack would work.
Apparently, the victim has to use Firefox 16 to access the attacker’s site. Then, if the user is signed in to Twitter, the attacker opens a new window in the social network from his own site and the target is redirected to a specially crafted URL containing a personal Twitter ID.
This allows the cybercriminal to harvest the victim’s personal Twitter ID.
Mozilla rushed to address the issue before cybercriminals got around to exploiting the vulnerability in the wild.
 14 DAY TRIAL //
14 DAY TRIAL //