Despite its alleged author being arrested, the Blackshades RAT (W32.Shadesrat) is still popular among cybercriminals. In fact, experts say they’ve spotted an increase in its usage over the past five months.
According to Symantec, the cybercrime tool is still being sold and used, despite reports of its author’s arrest, and despite the fact that its source code was leaked back in 2010.
After investigating the command and control (C&C) servers used in the attacks, researchers have found a link between Blackshades RAT and the Cool Exploit Kit. Cool has been utilized by cybercriminals to distribute not only W32.Shadesrat, but also other pieces of malware.
This happened until recently when the exploit kit’s creator, Paunch, was arrested by Russian authorities. After BlackHole and Cool disappeared from the market, the Neutrino exploit kit took their place.
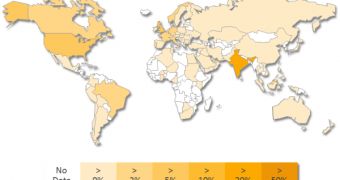
Most W32.Shadesrat infections have been spotted in India, the United States, and the United Kingdom. The threat is being used to steal credentials for email services, FTP clients, instant messaging apps and Web services from infected devices.
Hundreds of C&C servers on which the stolen information is uploaded have been identified. Most of these servers have been found to host exploit kits at some point.
As far as the location of these servers is concerned, most of them are in Lithuania and the United States.
“The distribution of the threats suggests that the attackers attempted to infect as many computers as possible. The attackers do not seem to have targeted specific people or companies,” Symantec’s Santiago Cortes noted in a blog post.
He added, “This demonstrates how complete the threat landscape is, as well as the resources that attackers have at their disposal.”
 14 DAY TRIAL //
14 DAY TRIAL //