Michal Zalewski, aka lcamtuf, a Polish Information Security Engineer at Google, has demonstrated the presence of a vulnerability in popular web browsers that could allow cybercriminals to serve their malicious elements to unsuspecting users who are led to believe that they’re downloading the files from legitimate sources.
“It is an important and little-known property of web browsers that one document can always navigate other, non-same-origin windows to arbitrary URLs,” the researcher said.
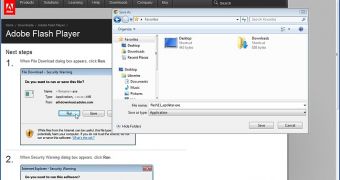
To prove his point, Zalewski has made a simple webpage that contains only a button. Once clicked, the “victim” is taken to the official Adobe Flash Player download site where he/she is served the software’s installer.
At least that’s how it looks, because in reality flash11_updater.exe is not the legitimate Flash Player, but a Calculator program. Of course, the demo is harmless, but the innocent executable can easily be replaced with a piece of malware in a real attack.
“All the top three browsers are currently vulnerable to this attack; some provide weak cues about the origin of the download, but in all cases, the prompt is attached to the wrong window - and the indicators seem completely inadequate,” the expert explained.
“The problem also poses an interesting challenge to sites that frame gadgets, games, or advertisements from third-party sources; even HTML5 sandboxed frames permit the initiation of rogue downloads (oops!),” he added.
The problem has been reported to Google, Microsoft and Firefox approximately one month ago. The responses are “fine” according to Zalewski, but only Chrome has actually planned a fix for the vulnerability.
While it’s true that there’s a certain degree of social engineering involved in these attacks, we presented numerous examples in the past in which users were easily convinced to click on apparently legitimate links or buttons.
Take a look at Zalewski’s clever proof-of-concept.
 14 DAY TRIAL //
14 DAY TRIAL //