The latest stable version of Microsoft’s Enhanced Mitigation Experience Toolkit (EMET) has been found to be susceptible to public exploits, which can completely disarm its protection.
Researchers at Offensive Security selected an older exploit that leveraged a weakness in the way Internet Explorer 8 handled the objects in memory in order to bypass ASLR (address space layout randomization) and DEP (data execution prevention) security features, and they altered it to disable the protection offered by EMET.
Using the original exploit, the researchers hit a couple of dead ends because EMET thwarted their attempts to run arbitrary code through HeapSpray and StackPivot mitigation techniques.
Since bypassing the protections one by one did not seem like a valid approach, they started to think of a way to disable all of them at once, by disarming EMET.
They found a global variable in the “.data” section in “EMET.dll” that can turn on or off all ROP (return-oriented programming) protections at runtime. Eliminating it completely would cause all ROP mitigations implemented by EMET to be disabled.
“This requires an attacker to build a ROP chain that will dynamically retrieve the base address of EMET.dll and overwrite the global variable with a zero,” the Offensive Security post says.
The method worked in the debugging environment and the command-line became available, but running the exploit outside the debugger caused EAF (export address filtering) to kick in.
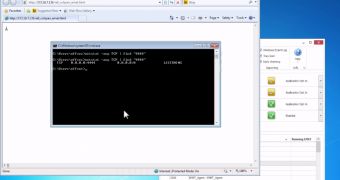
However, since there are various methods to disarm EAF, the researchers continued the experiment and managed to get shell access outside the debugger. The entire exploit code for disarming EMET 4.1.x is publicly available.
The exploit affects Internet Explorer 8 and has been tested on Windows 7, which appears to be the prevalent combination among computer users.
According to statistics provided by NetMarketShare, Internet Explorer 8 accounts for 21.25%, the largest chunk of the total browser market, followed at a safe distance by IE 11.
They also put Windows 7 in the lead as far user preference of the operating system is concerned, with a market share of 50.55%.
Although Offensive Security has not encountered such an exploitation method for disabling EMET in the public database, they do believe that Microsoft is well aware of the possibility because they plugged the holes in the upcoming version of the security kit.
They label EMET as a good tool that can challenge exploit developers, but it should not be regarded as a full solution. “What this shows is that while EMET is definitely a good utility and raises the bar for exploit developers, it is not a silver bullet in stopping these types of attacks,” they say.
A video showing the exploit in action is available below:
 14 DAY TRIAL //
14 DAY TRIAL //