Two-factor authentication (2FA) solutions provider Duo Security has identified a vulnerability in its WordPress plugin that can be exploited to bypass the second factor authentication on some deployments. Duo WordPress plugin 1.8.1 and earlier versions are affected.
The company has clarified that only WordPress “Multisite” configurations are impacted, and only if the plugin is not enabled globally. Sites on which the plugin is not enabled on an individual basis, and “Normal” WordPress deployments are not affected.
While the flaw can be exploited to bypass 2FA, an attacker would still need to know the primary authentication credentials.
In its security advisory, Duo describes the following attack scenario:
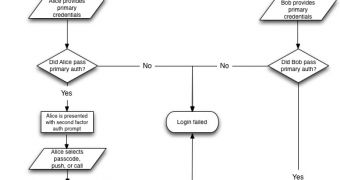
“A multisite WordPress deployment has two sites, Site1 and Site2, with the Duo WordPress plugin enabled for Site1 but disabled for Site2. Under normal circumstances, users logging into Site1 will be prompted for primary credentials and second-factor authentication; Site2 users will be prompted only for primary credentials.
A Site1 user may force-browse to the login URL of Site2, which will authenticate the user (as part of the same Wordpress multisite network), and redirect them back to Site1, without prompting for second-factor authentication.”
Interestingly, Duo Security says the vulnerability doesn’t affect only its product. Instead, it plagues 2FA plugins from other vendors as well. These companies have also been notified of the existence of the security hole.
The issue was discovered on February 6. While a permanent fix is rolled out, Duo Security advises customers to enable the plugin globally on “Multisite” configurations. Users are also recommended to disable 2FA for specific roles that don’t require it.
Additional technical details on the Duo Security 2FA WordPress plugin vulnerability are available in the advisory published by the company.
 14 DAY TRIAL //
14 DAY TRIAL //