Click fraud still represents an efficient way for cybercriminals to make money. Experts have been analyzing the activities of cybercriminals that rely on the Trojan dubbed Viknok for click fraud operations.
Trojan.Viknok has been around since at least April 2013. According to Symantec, the threat is capable of turning infected computers into botnet zombies by obtaining elevated privileges on the operating system, including on the 32- and 64-bit versions of Windows 7.
Last month, researchers noticed a considerable increase in the number of infections. In many cases, victims report hearing audio clips through their speakers when their systems are infected with the Trojan.
A total of 16,500 unique victims have been recorded in May alone, most of them being located in the United States.
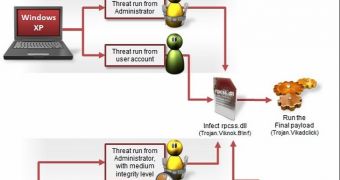
Viknok infects computers by injecting its payload into DLL files. However, on the latest operating systems, this is not an easy task. This is why cybercriminals are using a number of methods to inject files, such as rpcss.dll, a library that lets software run each time the operating system is started.
The threat uses the SeTakeOwnerhipPrivilege function to take ownership of system files. It also leverages the Dynamic-Link Library Search Order to run a malicious DLL inside the System Preparation Tool process. The RunLegacyCPLElevated.exe (Run a legacy CPL elevated) tool is utilized to execute DLLs with elevated privileges.
Another technique, which Symantec experts say is the most powerful, involves the exploitation of CVE-2013-3660, a Windows Kernel “Win32k.sys” local privilege escalation vulnerability.
When it first lands on a computer, Viknok uses one or more of these techniques to inject the rpcss.dll file. This allows the malware to execute every time the operating system starts. Once this file is infected, it loads the core of the malware, which is located in the System folder in an encrypted file.
“In many cases, the infection process is completely stealthy; the threat does not show any warning to the user. The malware is also difficult to detect since it does not show any suspicious running process, nor does it infect any of the standard load points,” Symantec experts note in their report.
In some instances, a User Account Control (UAC) prompt is displayed, and the victim needs to grant permission in order for the infection to be successful. However, the UAC prompt might not look suspicious, so users might give the Trojan permission without giving it too much thought.
As far as click fraud is concerned, once the threat infects a computer, its masters send it commands to load various websites. Experts believe victims might be hearing audio clips in their speakers because the content is played on the websites visited by Viknok. The websites offer car insurance, travel tickets, domain name registration, and many other services.
The number of infections has increased over the past months. If in December almost no infections were spotted, in January, the number increased to over 10,000. In February it dropped to around 2,500, but in March it increased to 7,500. In April, the total number of unique infections was 22,000.
 14 DAY TRIAL //
14 DAY TRIAL //