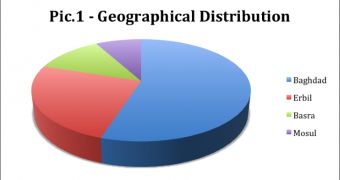
Malicious cyber-incidents started to record an upward trend, with activity concentrating in Baghdad, Erbil, Basra, and Mosul.
Los Angeles-based cyber-threat intelligence firm IntelCrawler reports that the malicious activities within the Iraqi ISP sector have intensified in the last two months and that multiple new botnets have emerged.
Attackers rely on dynamic DNS services to communicate with the infected machines. Based on the recent geo-political conflicts in the area, the company speculates that these computers could have been used in cyber-espionage campaigns and targeted multi-stage attacks.
IntelCrawler says that many of the malicious domain names used as command and control servers were registered with free public DNS providers. “The resolved IP addresses were related to subnets of various regional ISPs in Iraq, such as GORANNET, IQ-EARTHLINK, IQNETWORKS, IQ-NEWROZ and IQ-TARINNET,” says the company in a blog post. A chart showing the malicious activity recorded per ISP puts GORANNET ahead of others.
The strongest malicious activity has been recorded in Baghdad, with more than 50%, followed at a safe distance by Erbil, Basra, and Mosul.
As far as the threats used for malicious purposes are concerned, the security firm notes numerous remote administration toolkits “using Secure Sockets (SOCKS) and FTP/HTTP BackConnect with embedded file system browser for infected victims remote monitoring masked under Google Chrome and publicly available software.”
It seems that Microsoft’s recent seizure of 23 No-IP domain names has contributed to decreasing the malicious activity in the area because the cyber-attacks were conducted using NJrat as well.
NJrat is part of the Bladabindi malware family, which has been under close monitoring from Micrososft since December 2012.
Recently, the Redmond company served a federal court order to No-IP that allowed it to route traffic through its own infrastructure in order to identify bad traffic and sinkhole it to interrupt communication between the infected machine and the command and control server.
This particular type of threat has been observed during the Syrian conflict, employed against the Syrian opposition groups.
Small Office/Home Office (SOHO) routers in the IPv4 range of Iraq have been compromised by exploiting flaws in UPnP and through brute-forcing techniques. The attacks were targeted and a potential risk is mass network traffic surveillance.
“The share of Iraqi-based bad actors involved into various illegal activities in cyberspace acting as mercenaries seems to have significantly increased. Most appear united with Egypt, Lybian, Lebanese, Iranian, Syrian and various distributed Islamic groups performing targeted attacks because of religious and political motivation supported by state parties,” reads the report.
 14 DAY TRIAL //
14 DAY TRIAL //