A group of cybercriminals that uses the Cutwail spam botnet to distribute malware has switched from BlackHole to the Magnitude (Popads) exploit kit.
Ever since the author of BlackHole was arrested, cybercriminals are trying to find a replacement for it. At least one group has started using Magnitude, researchers from Dell’s SecureWorks report.
The spam campaign they’ve analyzed relies on bogus Pinterest emails that lead to a fake browser update website.
The Magnitude exploit kit is utilized to install the ZeroAccess Trojan by leveraging various vulnerabilities that might plague the victim’s system.
“Cybercriminals quickly adjusted their operation to maintain continuity. Combining social engineering with exploit kits sets the stage for a successful campaign and maximizes the potential for infecting as many victims as possible,” SecureWorks’ Counter Threat Unit (CTU) research team noted in a blog post.
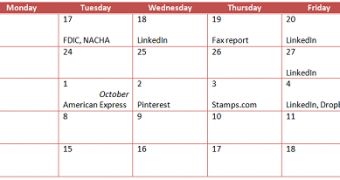
In the meantime, Trend Micro experts report that all significant BlackHole spam runs have ceased. A calendar published by the company shows that all the major spam campaigns have stopped following the arrest.
On underground forums, many cybercriminals are discussing the news of Paunch’s arrest. Some are concerned that the arrest of the exploit kit’s author might lead to the identification of BlackHole users, especially since the database that contains the list of clients is likely in the possession of law enforcement authorities.
Russian authorities still haven’t revealed Paunch’s real name or details of the arrest. Some commentators believe he might get a suspended sentence and a job with Russia’s Federal Security Service (FSB).
“In the long term, the impact of BHEK’s apparent demise remains somewhat unclear. Other exploit kits are available, but these may not have the support structure that Paunch was able to build with BHEK,” Trend Micro’s Jonathan Leopando noted.
 14 DAY TRIAL //
14 DAY TRIAL //