Almost one and a half month since its publishing, the Shellshock vulnerability in Bash, the default command line interpreter in Linux, has become mainstream, with scans in excess of 630,000 being recorded in the wild in a period of just two weeks.
The incidents originate from more than 15,000 IP addresses across the world (more than 95% being malicious requests), showing an exponential increase in the number of attackers compared to the early days of the disclosure, when over 890 IPs carried out attacks, as per Incapsula’s reports.
Attacks are almost as frequent as in the beginning
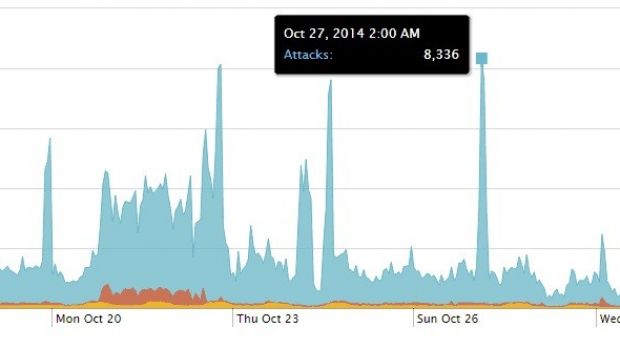
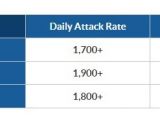
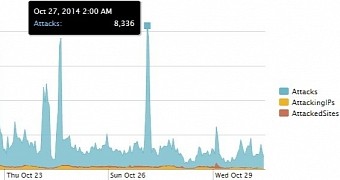
According to the statistics from the company, its systems were hit at the beginning at a rate of 1,970 attacks per hour, although some of them were the result of legitimate scanning tools.
Over one month after the initial incidents, the attack rate has not come down too much, over 1,870 being carried out. However, the difference consists in the fact that the amount of IP addresses deploying them has increased incredibly, by more than 1,600%.
This means that the crooks are scanning the Internet systematically in search of vulnerable machines that can be used for malicious activities.
One would think that, after all this time, most of the machines have been immunized against Shellshock; but not all systems online are taken care of on a regular basis, leaving them susceptible to attacks.
More than this, the initial patch for Shellshock did not mitigate the issue completely and the risk still existed.
Any system can be leveraged by crooks
“The media may have moved on, but the hackers haven’t. Shellshock remains an extremely dangerous vulnerability, having the ability to cause direct damage to unprotected devices, in addition to downstream collateral damage to others (e.g., as the result of a subsequent DDoS botnet attack),” Ofer Gayer and Igal Zeifman say in a blog post.
Any machine is an asset for cybercriminals, no matter how old it is, as the simple fact that it is connected to the Internet is enough for initiating or spreading an attack.
The attacks leveraging the Shellshock bug differ in purpose and in many cases the goal was to enslave the systems into a botnet; subsequent uses of the botnet range from launching distributed denial-of-service (DDoS) attacks to spreading malware.
Servers were among the most targeted because an attack on them requires less resources and the effect is the delivery of malware to visiting customers.
NAS devices were also in the crosshair because of the slew of files they store. Attackers could use the bug to plant crimeware with encryption capabilities in order to get a ransom fee in exchange for the decryption key.
 14 DAY TRIAL //
14 DAY TRIAL //