Although the entire industry is looking into means to make cloud services more secure than before, there still are vulnerabilities that need to be addressed.
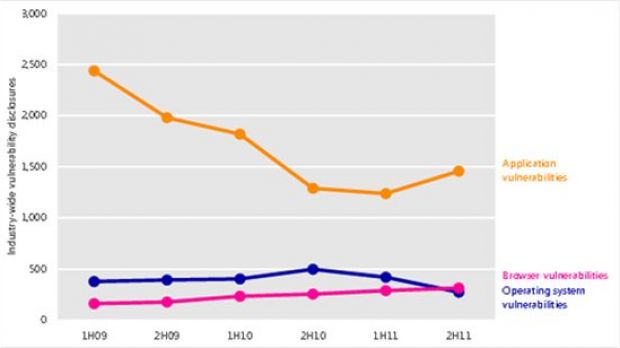
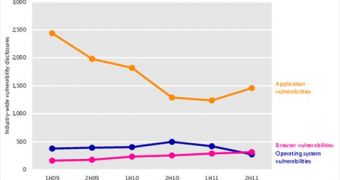
The trend shows that there are a lower number of vulnerability disclosures, but that does not mean that there aren’t issues to be concerned of.
In fact, thousands of such security breaches are being disclosed every six months in the software available out there, Tim Rains, director, Trustworthy Computing, notes in a recent blog post.
Most of these affect applications, with disclosures both in cloud services and traditional “boxed” software products. In fact, the number of vulnerabilities has increased 17.8 percent in the second half of 2011 (2H11), Rains explains.
Offering as example simple code that was meant to decide whether the user should receive access to the application or not, he presents a vulnerability that can prove hard to find when using code reviews or tools, or both.
“The problem in this code is that the function (AccessCheck()) that the developer is using to decide whether to grant access to the user, can fail for many reasons, many of which are not conditions related to denying access,” Rains continues.
“For example, if the application runs out of memory for any reason during this operation, the function could return an ‘out of memory’ error instead of the ‘access denied’ error that the developer was expecting.”
“Because the developer only checks for an ‘access denied’ error, this code will grant access to the user if any error other than ‘access denied’ error is returned. This is, therefore, a vulnerability that could potentially be exploited if an attacker could create the right conditions.”
In the latest installment of the Cloud Fundamentals Video Series, Rains discusses with Dennis Hurst, enterprise security products district manager at HP and Cloud Security Alliance member the manner in which cloud providers could address these issues using a set of operational security controls.
“If you don’t create an application that’s secure from the start it’s very, very difficult to take that and operationally secure it,” Denis Hurts replied.
Have a look at the video embedded above to learn more on the matter. You can also access more videos in the Trustworthy Computing Cloud Fundamentals Video Series for info on other aspects related to the security of cloud services.
 14 DAY TRIAL //
14 DAY TRIAL //