In the source code of the EDK1 project there is a reference implementation of the unified extensible firmware interface (UEFI) that contains a buffer overflow vulnerability, two security researchers discovered.
The EDK project is an open source, cross-platform solution for firmware development, used in some commercial UEFI implementations by different system vendors.
Exploit depends on how early the buggy code runs
The flaw was discovered by Rafal Wojtczuk (Bromium) and Corey Kallenberg (The MITRE Corporation), who said that the weakness was present in the Edk1/source/Sample/Universal/Variable/RuntimeDxe/FS/FSVariable.c source file.
According to Kallenberg, the buffer overflow is associated with one variable, intended for reclaiming unused space on the SPI flash chip in order to make room for creating other, larger variables.
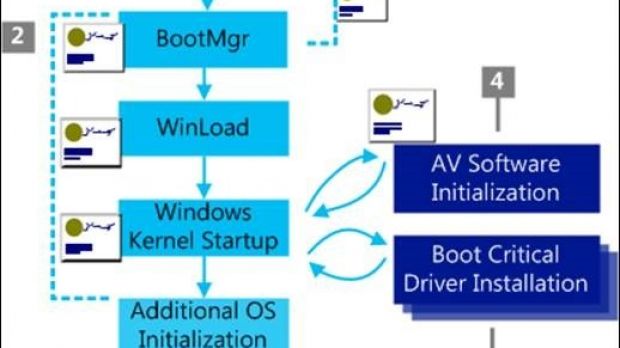
The two researchers say that the severity of this security flaw “depends on the earliness at which the vulnerable code can be instantiated,” because the boot sequence has multiple stages and the system becomes more secure as the process advances, locking down access to SPI Flash that contains the platform firmware, SMM, and other chipset configurations.
For a successful attack scenario, the vulnerable code should run before the SPI flash lock-down, which would give the possibility to replace the original firmware of the machine. Should this happen, the attacker would gain permanent access to the system, as subsequent security measures would deploy after this stage of the boot process and the compromise cannot be detected.
New firmware released for affected product
“Another possibility is for the attacker to leverage this vulnerability to get into SMM (if SMM [System Management Mode] is not sufficiently locked down yet), or to defeat Secure Boot and launch an authorized boot loader,” the researchers say in an advisory from the CERT (Computer Emergency Response Team) division at Carnegie Mellon University.
Exploitability of the bug depends on the firmware implementation for each OEM (original equipment manufacturer).
As per the CERT advisory, one vendor whose product is vulnerable to this type of attack is Insyde Software Corporation. The company has issued a fix for the problem, though, and users are urged to apply it.
Wojtczuk and Kallenberg are also credited for reporting another UEFI-related vulnerability, which allows an attacker to access the boot script, offering the possibility to bypass Secure Boot and tamper with the firmware.
The vendors affected by this flaw have released updated firmware code and are working with OEMs to incorporate it in the new machines.
 14 DAY TRIAL //
14 DAY TRIAL //