Security researchers have uncovered a new strain of banking malware that comes with network sniffing capabilities for stealing financial credentials.
Once installed on the victim’s computer, the malware starts capturing and logging all outgoing network traffic. The worst thing is that the malicious tool has the capability to extract data sent over a secure connection because it can hook into multiple network components in order to monitor the traffic on the network.
Researchers at Trend Micro say that the new threat, identified as EMOTET, infects the machine through an email message carrying a malicious link that purports to lead to details relating to a financial transaction.
Instead, users are taken to compromised addresses from where the malware can be downloaded.
Trend Micro Threat Response Engineer Joie Salvio says that as soon as the malicious file reaches the computer, it starts downloading the additional components, which include a file with the targeted financial institutions.
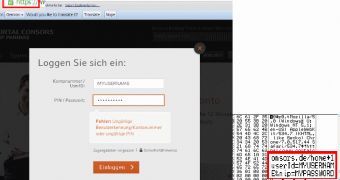
The sample analyzed by the researchers was designed to steal credentials for logging into the accounts of several German banks, but they warn that the configuration file may vary and that other institutions could also be in the crosshairs.
Among the files downloaded through the dropper there is “a .DLL file that is also injected to all processes and is responsible for intercepting and logging outgoing network traffic.”
Injected into a web browser, the DLL checks the accessed websites with the URLs targeted by the malware and, if a match is found, all the information sent to the address is retrieved. Salvio says that EMOTET “saves the whole content of the website, meaning that any data can be stolen and saved.”
It appears that an encrypted connection is not an impediment for the data to be stolen as Trend Micro researchers found that the credentials used to log into a service using HTTPS were captured by the malware.
They note that stealing sensitive information this way does not trigger any alert because the user receives no sign of suspicious activity and everything looks normal.
All the stolen information is first encrypted and then stored in a registry entry. This may be an anti-detection measure for file-based antivirus solutions.
Although EMOTET seems to focus on German banks, infections have been observed in the EMEA (Europe, the Middle East and Africa) region. However, its activity has been detected in the Asia-Pacific and North America.
This threat is distributed mostly through fake emails and users are advised to refrain from clicking links in suspicious messages, as well as to reject any downloads from shady web locations.
 14 DAY TRIAL //
14 DAY TRIAL //